Found via Digg: http://video.google.com/videoplay?docid=5579362191486305681&q=hyperland
A documentary made in 1990 that was pretty interesting. Its good to see some Tom Baker footage.
Monday, December 11, 2006
Friday, December 08, 2006
December 8, 1941

Those who do not remember the past, are doomed to repeat it. Here's how a competent administration responds to attack...
Franklin Delano Roosevelt: Pearl Harbor Address to the Nation
(Yes... I know Pearl Harbor was bombed on the 7th... the speech was on the 8th)
It took hard work and sacrifice from the entire nation, but we had good solid leadership that we could trust to do the right thing back then.
Let's never forget the sacrifices made to win our freedom.
More HP crap
I've previously offered up the remains of my old laptop for anyone who personally needs them. Derrick wrote seeking out a power connector... which doesn't suprise me... they put the connector in the corner of the motherboard... a poor choice because its weaker, and the cord is more likely to be stressed laterally as well.
Here's my suggestion back to him....
Here's my suggestion back to him....
Hi Derrick,
No... the motherboard was the root of the evil... and was the main thing pitched...
You should be able to buy the connector, fairly cheap at any major supply house... have you tried Digikey? http://www.digikey.com/
This page of their catalog might be what you need.... not sure of the exact connector dimensions, as I no longer have the adapter. http://dkc3.digikey.com/PDF/T063/0337-0340.pdf
Section 12 on that page (right-angle PCB connectors)... may be it.
The dimensions are critical on those plugs... the wrong size just won't work.
Also... we've had some success re-soldering then EPOXYING the connector in place to relieve strain on my wife's laptop... it lasted at least 6 months... and now I need to repeat the process.
Good luck!
--Mike--
Monday, November 20, 2006
HP Pavilion DV5030US - Dead for the 3rd time!
Ugh... just as I was getting back into the swing of things, LaptopJenny (an HP Pavilion DV5030US notebook) died again!
I shipped it for repair on the 20th of last month... looks like I get to do it again...
Here's what the my Windows desktop looks like right now.... not very useful:

Here's what it's supposed to look like (if you push in the upper left corner, it works until you let go)
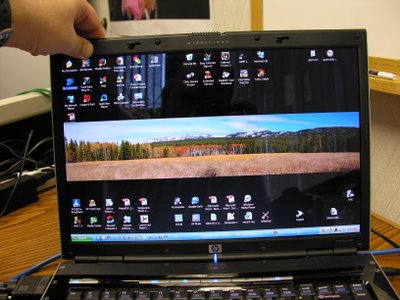
I'm hoping I get some other option than repair again!
I shipped it for repair on the 20th of last month... looks like I get to do it again...
Here's what the my Windows desktop looks like right now.... not very useful:

Here's what it's supposed to look like (if you push in the upper left corner, it works until you let go)

I'm hoping I get some other option than repair again!
Sunday, November 19, 2006
Aspen in the Grand Tetons
Noran was gracious and patient while I took a series of photos of this treeline, it was amazing in person, and the photo only begins to show how beautiful it really was.
This is somewhere near the Grand Teton mountains, I'm unsure of the exact location. We were on our way home, and a bit short on time.
This is a series of frames joined using AutoStitch, saturated a bit, then cropped.
This is somewhere near the Grand Teton mountains, I'm unsure of the exact location. We were on our way home, and a bit short on time.
This is a series of frames joined using AutoStitch, saturated a bit, then cropped.
Saturday, November 18, 2006
Robotic armies?
John Robb writes about the future of "Nano UAVs", which are very small flying robots. He, and his commenters are off the mark, though... they figure it'll only be large economic powers which can afford to make them.
John Robb, meet Make magazine, where hackers like myself shop for ideas and tools.
John Robb, meet Make magazine, where hackers like myself shop for ideas and tools.
Friday, November 17, 2006
Yet another online quiz
Your Ideal Relationship is Marriage |
 You've dated enough to know what you want. And that's marriage - with the right person. You're serious about settling down some time soon. Even if you haven't met the person you want to get hitched to! |
I'm a sucker for online quizes... it was hard to answer questions in retrospect... but I did.
Thursday, November 16, 2006
TrashCat
Found this over at Flickr... it's part of a big set.
http://flickr.com/photos/buro9/
I find it amusing, and I hope you will too.
http://flickr.com/photos/buro9/
I find it amusing, and I hope you will too.
I've got the power?!?!
According to the calculator attached to the tubes on the internets...
Your Power Level is: 70% |
 You're a very powerful person, and you know that all of your power comes from within. Keep on doing what you're doing, and you'll reach your goals. |
Wednesday, November 15, 2006
WiFi information on the Red Line
I was just about to get off the Red Line at work... when I noticed something different about the sign over the door.

Do you see it? It took a minute to come to a few realizations:


Do you see it? It took a minute to come to a few realizations:
- WiFi access got added to the station information - a welcome addition!
- The list included open and locked networks.... which was odd, but helpful
- The new data wasn't taped on top of an existing sign
- No official body in its right mind would post info about open WiFi points it didn't own, let alone locked ones it obviously doesn't own...
- Someone else put this sign here.

Sunday, November 12, 2006
The Miracle Of...
It was on our road trip out west to celebrate our 5th Wedding Anniversary that we found out Noran was pregnant.
On the way back home, we stopped in North Platte, Nebraska for the night. We decided to visit Cody Park, just a few blocks from our motel, to see the sights.
There is a VERY big steam engine and train there... so big I needed to get more distance to try to get it in...
I climbed the hill to get a better view of the train... and found this on the sidewalk...
The coincidence of finding this right after learning Noran was pregnant was enough to get me to take this photo.
I now wonder who made the drawing in the first place, and what their story is.
If you know anything about this, please write.
--Mike--
On the way back home, we stopped in North Platte, Nebraska for the night. We decided to visit Cody Park, just a few blocks from our motel, to see the sights.
There is a VERY big steam engine and train there... so big I needed to get more distance to try to get it in...
I climbed the hill to get a better view of the train... and found this on the sidewalk...
The coincidence of finding this right after learning Noran was pregnant was enough to get me to take this photo.
I now wonder who made the drawing in the first place, and what their story is.
If you know anything about this, please write.
--Mike--
Monday, November 06, 2006
Virginia's Baptism
I've finally uploaded some things to Flickr... the photos we gave to guests at Virginia's Baptism dinner. I've also uploaded some 117 photos taken that day.
Monday, October 30, 2006
Free at last!
Getting things in order
I noticed today that I couldn't drag and drop things on LaptopJenny... I investigated all sorts of things until deciding it was a device driver issue. I used Device Manager to remove the trackpad driver, and after two reboots, all was well.
I only realized after I was done that it had disabled both mouse buttons while the mouse moved... a supremely frustrating thing when you're used to them.
Next up, I just found SharePod, which will let me extract the music from the iPod Mini Noran gave me to replace the dead Shuffle, and I can use it without iTunes.
I hate iTunes... the stupid piece of shit always gets in the way, trying to connect to the iPod like a crazed Mother Bear protecting her young. Usually when I plug an iPod in, it's to charge it, or to transfer files in either direction.. NOT to put more overpriced crippled music in it.
iTunes is DefectiveByDesign!
I'm never going to fit the photos back in LaptopJenny... I've forgotten about music... I need my music!
Cest la vie
--Mike--
I only realized after I was done that it had disabled both mouse buttons while the mouse moved... a supremely frustrating thing when you're used to them.
Next up, I just found SharePod, which will let me extract the music from the iPod Mini Noran gave me to replace the dead Shuffle, and I can use it without iTunes.
I hate iTunes... the stupid piece of shit always gets in the way, trying to connect to the iPod like a crazed Mother Bear protecting her young. Usually when I plug an iPod in, it's to charge it, or to transfer files in either direction.. NOT to put more overpriced crippled music in it.
iTunes is DefectiveByDesign!
I'm never going to fit the photos back in LaptopJenny... I've forgotten about music... I need my music!
Cest la vie
--Mike--
Sunday, October 29, 2006
The odd twilight at the end of Democracy
It's now 1:45AM in Chicago, AND 1:45AM in New York City... the one odd hour a year when we're still in Daylight Savings Time, and they've left it behind.
Our country is doomed.... the FBI's second raid on Christopher Soghoian's residence is a big RED FLAG. Chris is a security researcher, a "white hat". He has a long record of helping to solve security problems. He pointed out just how insecure the whole "you must have a boarding pass" requirement is when it's not actually verified, by creating a fake boarding pass generator.
Instead of actually doing something to improve security, the FBI falls back on its long, LONG tradition of trying to use intimidation as a substitute for hard work.
I'm now convinced that our Democracy is very likey doomed... the election will be nullified by Diebold, and the avenues of redress for our grievances will evaporate. Unfortunately, this will leave us contemptating the stark implications of words of President John F. Kennedy:
We deserve a better country, a bright future. The peaceful revolution that occurs in every just election saves us all more horror than one can imagine. Lets hope we can continue in our great tradition of true Democracy.
--Mike--
Our country is doomed.... the FBI's second raid on Christopher Soghoian's residence is a big RED FLAG. Chris is a security researcher, a "white hat". He has a long record of helping to solve security problems. He pointed out just how insecure the whole "you must have a boarding pass" requirement is when it's not actually verified, by creating a fake boarding pass generator.
Instead of actually doing something to improve security, the FBI falls back on its long, LONG tradition of trying to use intimidation as a substitute for hard work.
I'm now convinced that our Democracy is very likey doomed... the election will be nullified by Diebold, and the avenues of redress for our grievances will evaporate. Unfortunately, this will leave us contemptating the stark implications of words of President John F. Kennedy:
Those who make peaceful revolutions impossible
will make violent revolutions inevitable.We deserve a better country, a bright future. The peaceful revolution that occurs in every just election saves us all more horror than one can imagine. Lets hope we can continue in our great tradition of true Democracy.
--Mike--
Saturday, October 28, 2006
LaptopJenny is back!
Now returned from her SECOND display repair is LaptopJenny... my HP DV5030US.
Unlike last time, I made a FULL backup of everything this time. This helped me greatly when, like last time, HP reformatted the hard drive. I'm very pleased with the way that Backup and Restore actually worked with Windows XP Media center on this thing. I've got all of my programs, desktop icons, network connections (VPN to work, etc).
I specifically haven't restored all the photos yet, because I can't. They just won't fit. I've got 18 Gigabytes of photos (1997-2003), and 10 remaing gigabytes to put them in. I've got too many picture.
I carry around, on a daily basis, some 80,000 photos. The common wisdom of photographers everywhere is that you can instantly double the quality of your collection by throwing away half. I've already done this, I have about 160,000 photos in the archive. (144 Gb!)
I did it the first time by just tossing out things that were out of focus, badly framed, etc. I wasn't all the way through, either... but I lost my place in the first HP format, so now I get to figure it out again. Not only that... now the pictures are ones I've already decided to keep once.
It's overwhelming if you look at the math. Reviewing them and making a decision for each photo might take 10 seconds each....800,000 seconds == 13,333 minutes == 380 South Shore commutes... yikes! If I focus on this, and spend most of my train commutes, I'll be done next year.
When I give out the number of photos on my laptop (Ctrl-T in ThumbsPlus)... I typically get a reaction of disbelief, and dismissal, which lasts only long enough for the slide shows to begin. (F8 in ThumbsPlus)... then a pleasant tour through some days events.... then thanks and appreciation... it's an emotional ride I've learned to enjoy taking.
It's a hell of a lot of fun to be able to pull out the laptop, and start a slide show for bored kids on the way to Chicago.. I do it about once ever other month. Now I'm showing a lot of photos of Virginia as well. In this way, LaptopJenny is a social tool, and not just a toy for playing RT3. It helps me to share a bit of my world with my friends and acquaintances.
I've been lax putting things up here... and on my Flickr account... I'm working on getting my life organized a bit more, so I'll try to get this going as well.
Unlike last time, I made a FULL backup of everything this time. This helped me greatly when, like last time, HP reformatted the hard drive. I'm very pleased with the way that Backup and Restore actually worked with Windows XP Media center on this thing. I've got all of my programs, desktop icons, network connections (VPN to work, etc).
I specifically haven't restored all the photos yet, because I can't. They just won't fit. I've got 18 Gigabytes of photos (1997-2003), and 10 remaing gigabytes to put them in. I've got too many picture.
I carry around, on a daily basis, some 80,000 photos. The common wisdom of photographers everywhere is that you can instantly double the quality of your collection by throwing away half. I've already done this, I have about 160,000 photos in the archive. (144 Gb!)
I did it the first time by just tossing out things that were out of focus, badly framed, etc. I wasn't all the way through, either... but I lost my place in the first HP format, so now I get to figure it out again. Not only that... now the pictures are ones I've already decided to keep once.
It's overwhelming if you look at the math. Reviewing them and making a decision for each photo might take 10 seconds each....800,000 seconds == 13,333 minutes == 380 South Shore commutes... yikes! If I focus on this, and spend most of my train commutes, I'll be done next year.
When I give out the number of photos on my laptop (Ctrl-T in ThumbsPlus)... I typically get a reaction of disbelief, and dismissal, which lasts only long enough for the slide shows to begin. (F8 in ThumbsPlus)... then a pleasant tour through some days events.... then thanks and appreciation... it's an emotional ride I've learned to enjoy taking.
It's a hell of a lot of fun to be able to pull out the laptop, and start a slide show for bored kids on the way to Chicago.. I do it about once ever other month. Now I'm showing a lot of photos of Virginia as well. In this way, LaptopJenny is a social tool, and not just a toy for playing RT3. It helps me to share a bit of my world with my friends and acquaintances.
I've been lax putting things up here... and on my Flickr account... I'm working on getting my life organized a bit more, so I'll try to get this going as well.
Thursday, October 26, 2006
Chicago

This is a small sample size of a much bigger photo I stitched together.
Update - December 20, 2007 - More Chicago photos from me on this blog, and at Flickr.
Tuesday, August 29, 2006
Flickr Maps - Geotagging Rocks!
It takes a lot of work, but Geotagging with Flickr (aka Flickr Maps) is pretty cool. Here's the map of the photos I've geotagged so far. It takes a while for the photos you tag to show up with everyone elses, so you have to be patient.
They do have a way to parse embedded GPS information from your photos, if present... but you have to turn it on.
Be careful about Geotagging your home, etc.
Thanks to DocSearls and ThomasHawk for pointing this out.
They do have a way to parse embedded GPS information from your photos, if present... but you have to turn it on.
Be careful about Geotagging your home, etc.
Thanks to DocSearls and ThomasHawk for pointing this out.
Monday, August 21, 2006
Bullshit driven genius
Today's idea, straight from the Web 2.0 bullshit generator
Just found another one
If we can build a DLL or library which can link Excel or Access to web services, we could make a mint.... this thing is starting to look like a really good source of ideas... (spooky, isn't it?)
integrate data-driven weblogsActually... it might be usefull to have a data logger create a web log, then use a google local search to index it for debugging and long term tracking purposes.... creativity comes from strange places... even bullshit generators.
Just found another one
disintermediate standards-compliant web services
If we can build a DLL or library which can link Excel or Access to web services, we could make a mint.... this thing is starting to look like a really good source of ideas... (spooky, isn't it?)
Sunday, August 20, 2006
Here come the activists mobs!
While its possible that Doc might be a gatekeeper... consider the alternative... activist mobs!
We face a future of politically driven activism similar to that which has the FCC censoring on the basis of "hundreds of complaints" which turn out to be from one source. This politically charged devisive form of astroturfing needs to be nipped in the bud.
I for one, think that a bit of careful gatekeeping might be in order!
Oh... the irony of it
We face a future of politically driven activism similar to that which has the FCC censoring on the basis of "hundreds of complaints" which turn out to be from one source. This politically charged devisive form of astroturfing needs to be nipped in the bud.
I for one, think that a bit of careful gatekeeping might be in order!
Oh... the irony of it
Wednesday, August 02, 2006
Slippery slopes - the 1st Amendment
Josh Wolf now sits in jail, and I think he's trying to defend the 1st amendment. I gave $20 to help his defense, I hope it helps.
Ryanne Hodson gives a good summary of my view:
In the comments to Scoble's post which is where I first read about it, the comments seem to be running toward the blogospheric default... quick reaction without digging in for details. The critical matter in this case isn't the tape, it's the federal attempt to override the states rights. The people of California have made a law to protect journalists from fishing expeditions, a shield law. The federal government is using a very flimsy argument about tax money to try to bypass the States right to self-govern.
Ryanne Hodson gives a good summary of my view:
record this and be harassed later on?” This is especially true during controversial political events.
Why should any of us care?
For us, it’s important to support journalists or anyone with a camera being harassed by the government to turn over recordings of public events that each of us has every right to record. We don’t want the government, local or federal, to make it a habit of asking for anything we happen to record. Then we each might question: “Do I want to
In the comments to Scoble's post which is where I first read about it, the comments seem to be running toward the blogospheric default... quick reaction without digging in for details. The critical matter in this case isn't the tape, it's the federal attempt to override the states rights. The people of California have made a law to protect journalists from fishing expeditions, a shield law. The federal government is using a very flimsy argument about tax money to try to bypass the States right to self-govern.
Bad Marketing, 101
I found a very good distillation of bad marketing, from Melinda, via way of Shelley in her critique of BlogHer:
Bad marketing is rude marketing. The abuse of trust demonstrated in the incident above, is exactly what drives people to generalize and hate all marketing. We need to stamp it out!
When it's done right, its all about condensing your message into a small gift, the gift of condensed truth. The lower the bullshit content, the more valuable for all. It saves time and effort for everyone.
Bad marketing is about trying to substitute bullshit for substance.
well.. that's the wandering for now
--Mike--
At another point, I was sitting in the audience waiting for a presentation to start, when a woman came up and knelt down by my side. She seemed friendly and I thought perhaps she'd seen my presentation on Day One, and wanted to chat about it. Or maybe she was familiar with my BlogHer posts…(emphasis mine)
I realized with a sinking feeling, as she handed me her card and a book, that she was making a one-to-one sales pitch. I politely accepted her "gifts", sensing she'd then move on to the next customer, and she did.
I came to BlogHer to meet other bloggers, not get tricked into a conversation that then turned into a sales pitch.
Bad marketing is rude marketing. The abuse of trust demonstrated in the incident above, is exactly what drives people to generalize and hate all marketing. We need to stamp it out!
When it's done right, its all about condensing your message into a small gift, the gift of condensed truth. The lower the bullshit content, the more valuable for all. It saves time and effort for everyone.
Bad marketing is about trying to substitute bullshit for substance.
well.. that's the wandering for now
--Mike--
Wednesday, July 26, 2006
Tuning loops, redux
Doc says that blogging is provisional. I take it that this is because it's part of a conversation. I can understand how he's saddened by the loss of the one good paper in his town, and the overall trend of the demise of local news. He's searching hard for technology, the net, or even smart mobs to replace it... he's searching in vain. The way we consume "news", is, in fact, the problem.
Cool hunting continous partial attention just isn't going to replace local news, no matter how you aggregate it. I'm never going to replace the local reporter with a beat to cover. Using technorati, digg, metafilter, or friends who forward me amusing links isn't going to do it either.
No matter how you slice or dice it... local news requires someone dedicated to the local beat. A real, live human being, who can always find other, more amusing things to do. So, we need to encourage all of the good local reporting we find. We also need to actively seek it out, and patronize it.
It turns out, the way this works in the blog-o-sphere is one already overlooked as old news.... hyperlinks and blogrolls. The fact is that what we pay attention to determines what we find. If we take the time to keep our reading lists reasonable, and up to date, we'll find a lot of value that we'd otherwise miss trolling digg for the next new thing.
I started this post last night, and as typical for Doc... he somehow does a zen reply to a post before I've even written it... today he writes about finding value via Ronni Bennet's favorites list... and behold, the circle is complete.
The act of blogging, and keeping your blogroll and web site up to date are creative. Sucking down RSS feeds and cool hunting are consumptive. It's better to create.
Doc, the replacement for local newspapers is blogs and blogrolls... the tools still need work, and we still need to find social incentives to appreciate quality, and reward effort... but you've already found the answer... you just don't know it yet.
--Mike--
Cool hunting continous partial attention just isn't going to replace local news, no matter how you aggregate it. I'm never going to replace the local reporter with a beat to cover. Using technorati, digg, metafilter, or friends who forward me amusing links isn't going to do it either.
No matter how you slice or dice it... local news requires someone dedicated to the local beat. A real, live human being, who can always find other, more amusing things to do. So, we need to encourage all of the good local reporting we find. We also need to actively seek it out, and patronize it.
It turns out, the way this works in the blog-o-sphere is one already overlooked as old news.... hyperlinks and blogrolls. The fact is that what we pay attention to determines what we find. If we take the time to keep our reading lists reasonable, and up to date, we'll find a lot of value that we'd otherwise miss trolling digg for the next new thing.
I started this post last night, and as typical for Doc... he somehow does a zen reply to a post before I've even written it... today he writes about finding value via Ronni Bennet's favorites list... and behold, the circle is complete.
The act of blogging, and keeping your blogroll and web site up to date are creative. Sucking down RSS feeds and cool hunting are consumptive. It's better to create.
Doc, the replacement for local newspapers is blogs and blogrolls... the tools still need work, and we still need to find social incentives to appreciate quality, and reward effort... but you've already found the answer... you just don't know it yet.
--Mike--
Sunday, July 09, 2006
Wild Lily
I cleaned up the background on this Wild Lily growing by our air conditioner. It's one of a set of photos of the Lillies in our yard which I uploaded to Flickr today.
Thursday, June 29, 2006
Credit cards and identity
Doc Searls posts his thoughts about identity at IT Garage. My interpretation of the discussion so far is one of the need to gain some control. I'd like to propose a modest shift which might help the most expensive part of Identity problem, credit cards.
Current credit card systems rely mostly on one thing... keeping a secret. The secret consists some fairly public information (Name, Address) and a true secret (the account number). Insofar as the company is concerned, this is the ONLY key required to make transactions as part of your relationship with them.
I believe it's all this way because of inertia... perhaps I'm wrong, but it seems very quaint and obsolete to me.
Because there is really only one secret number, you have no way of keeping your identity separate as far as the credit card system is concerned. The companies like to pretend their is a difference between the card holder, and a vendor, because it helps maintain the illusion that the system is secure.
Every time you give your account number to someone, for all intents and purposes, you give them your identity. Furthermore, they can use it later, at any point in time or space until the expiration date, without restriction. Your identity gets propogated everywhere, in their backups, on the laptop their webmaster uses to update things, and the person who buys the hard drive after he upgrades. ANY of those people can use your identity.
It's just not possible to keep all of these copies secure. It's stupid to try if there are alternatives available.
For basic transactions, I propose a change to the model... non trival, to say the least, but relatively simple to implement and execute. Allow us to use one time keys for each and every transaction. Don't allow it to be reused, EVER. This makes the value of an old key go to zero, as soon as it gets used.
This makes the worry about the secret getting stolen go away. 8)
Relationships require more detail, as they extend over time, and include a much bigger chunk of information. I'd still go with the one time secret, but keep the terms and conditions transparently available to BOTH parties at the credit company site. The customer needs to be able to track and modify the conditions as time progress, and it's logical that the credit card computer is the place to do this.
If the key gets locked down to a specific vendor account, the value to thieves goes down dramatically (not to zero, but substantially none the less). This makes the worry about the key getting stolen go down proportionally as well.
Those are my thoughts about it. I'm not calling for new infrastructure, and I don't even begin to deal with Single Sign On... but I do address the most expensive mess related to identity (I think).
I'm curious to see how this gets remixed.
--Mike--
Current credit card systems rely mostly on one thing... keeping a secret. The secret consists some fairly public information (Name, Address) and a true secret (the account number). Insofar as the company is concerned, this is the ONLY key required to make transactions as part of your relationship with them.
I believe it's all this way because of inertia... perhaps I'm wrong, but it seems very quaint and obsolete to me.
Because there is really only one secret number, you have no way of keeping your identity separate as far as the credit card system is concerned. The companies like to pretend their is a difference between the card holder, and a vendor, because it helps maintain the illusion that the system is secure.
Every time you give your account number to someone, for all intents and purposes, you give them your identity. Furthermore, they can use it later, at any point in time or space until the expiration date, without restriction. Your identity gets propogated everywhere, in their backups, on the laptop their webmaster uses to update things, and the person who buys the hard drive after he upgrades. ANY of those people can use your identity.
It's just not possible to keep all of these copies secure. It's stupid to try if there are alternatives available.
For basic transactions, I propose a change to the model... non trival, to say the least, but relatively simple to implement and execute. Allow us to use one time keys for each and every transaction. Don't allow it to be reused, EVER. This makes the value of an old key go to zero, as soon as it gets used.
This makes the worry about the secret getting stolen go away. 8)
Relationships require more detail, as they extend over time, and include a much bigger chunk of information. I'd still go with the one time secret, but keep the terms and conditions transparently available to BOTH parties at the credit company site. The customer needs to be able to track and modify the conditions as time progress, and it's logical that the credit card computer is the place to do this.
If the key gets locked down to a specific vendor account, the value to thieves goes down dramatically (not to zero, but substantially none the less). This makes the worry about the key getting stolen go down proportionally as well.
Those are my thoughts about it. I'm not calling for new infrastructure, and I don't even begin to deal with Single Sign On... but I do address the most expensive mess related to identity (I think).
I'm curious to see how this gets remixed.
--Mike--
Wednesday, June 28, 2006
Tuesday, June 27, 2006
Subversion Rocks!
I've been using Subversion, also known as SVN in a stand alone configuration on my laptop, and it's nice to be able to undo, and keep track over version. Today though, I took it to a new level.
I'm pulling work stuff off my laptop, and onto the servers here where it belongs. I installed SVN and used SVNserve to run it as a service. Once I got the kinks worked out, I was able to check out and commit from multiple places across the local network, and let me say... it ROCKS!
I've got one heck of a backup strategy in place for my code now, thanks to this thing. One small piece of my life firmly in control.... many more to go.
I'm pulling work stuff off my laptop, and onto the servers here where it belongs. I installed SVN and used SVNserve to run it as a service. Once I got the kinks worked out, I was able to check out and commit from multiple places across the local network, and let me say... it ROCKS!
I've got one heck of a backup strategy in place for my code now, thanks to this thing. One small piece of my life firmly in control.... many more to go.
Monday, June 26, 2006
Internet incantations
Dave suggests that the internet culture results in "A network a mile wide and nanometer deep".
I'd say that he's got a valid point, one that I won't dispute.
I will say that the internet makes it possible to lower the cost of keeping relationships that might otherwise get lost over time. I'm only now (at 42) starting to learn the value of keeping such friendships, and attempting to ween myself off of my hyperextended period of indifference.
I think that the tools are just that... tools. Like the atomic bomb, they do have some moral dimension of their own, but it is overwhelmingly up to the people and societies that decide how they are to be employed that bear the ultimate responsiblity. If we choose to bury ourselves in distractions, we'll get what we want. If we choose to do the other thing, and seek knowledge and growth, and nurturing of relationships, we'll get that as well.
The internet is a tool... not a silver bullet, which I believe is a view we can all share.
I'd like to mix in my interpretation of Ethan Johnson's "physical symbolism", like this:
Doc Searls has vision of the world as he wishes it to be. He consistently expresses and refines this view. The act of sharing and promoting the idea is a type of incantation, a type of magic for lack of a better term... the act of reciting and repeating this vision will eventually cause it to become manifest in reality. How quickly this happens, and how much of an actual difference it makes in the overall scheme of life, is best analyzed post facto (say 20 years from now).
We're all making incantations of what we'd like the world to be... its very important to be careful what you wish for, you just might get it.
Thanks Dave, Doc and Ethan for the pointers, and the bits of wisdom.
--Mike--
I'd say that he's got a valid point, one that I won't dispute.
I will say that the internet makes it possible to lower the cost of keeping relationships that might otherwise get lost over time. I'm only now (at 42) starting to learn the value of keeping such friendships, and attempting to ween myself off of my hyperextended period of indifference.
I think that the tools are just that... tools. Like the atomic bomb, they do have some moral dimension of their own, but it is overwhelmingly up to the people and societies that decide how they are to be employed that bear the ultimate responsiblity. If we choose to bury ourselves in distractions, we'll get what we want. If we choose to do the other thing, and seek knowledge and growth, and nurturing of relationships, we'll get that as well.
The internet is a tool... not a silver bullet, which I believe is a view we can all share.
I'd like to mix in my interpretation of Ethan Johnson's "physical symbolism", like this:
Doc Searls has vision of the world as he wishes it to be. He consistently expresses and refines this view. The act of sharing and promoting the idea is a type of incantation, a type of magic for lack of a better term... the act of reciting and repeating this vision will eventually cause it to become manifest in reality. How quickly this happens, and how much of an actual difference it makes in the overall scheme of life, is best analyzed post facto (say 20 years from now).
We're all making incantations of what we'd like the world to be... its very important to be careful what you wish for, you just might get it.
Thanks Dave, Doc and Ethan for the pointers, and the bits of wisdom.
--Mike--
Friday, June 23, 2006
Virtual BloggerCon
Thanks to Doc's timely notice, I'm virtually in San Francisco, (or so they say)... at BloggerCon... Doc Searls is doing a bang-up good job taking notes (he's just done with tools), and showing up on the IRC at times.
It's fun to actually converse with technological peers... doesn't happen much at work, where I'm the whole IT staff.
--Mike--
It's fun to actually converse with technological peers... doesn't happen much at work, where I'm the whole IT staff.
--Mike--
my themes...
Things I keep bringing up, over and over... all in one handy posting:
--Mike--
- HTML doesn't allow markup of documents (take a web page, save it on CD-R)... now tell me how I can highlight part of it... (I CANT!)
- There needs to be a way to jump into existing content like Video, MP3 via external hyperlink
- Credit Card systems based on keeping your SSN or Card # secret are insanely insecure, and need to go
- We got a wake up call in 1970 to cut our dependence on foreign energy... why haven't we?
- 90% of all stuff on the web is crap... including this
- I'm a very lucky man... inspite of all my complaining, I try to be grateful every day for Noran and Virginia
- Computers are tools, the means, not the ends
- Users shouldn't take the blame for bad tools
- Why can't someone come up with a database that syncs to laptops?
- Tags and metadata are great, but take wayyy to much time to create
--Mike--
Thursday, June 22, 2006
Not even a cheese sandwich
One of the interesting changes that Virginia brought to us is the sudden need to immerse ourselves in deep knowledge of her inputs and outputs. These need to be cafefully monitored and managed, to avoid many issues.
Recently, she had a bit of an output backlog. This is normal for infants of her age, but still managed to concern us, primarily via the lack of a sleep state that this caused. Our subsequent exhaustion then cause a ripple through our I/O as well.
We were relieved when her distress ceased, and the output queue was cleared. We had a visit with the diagnostician today, who monitors her functions and growth. She's progressing quite well, and we're performing our management and maintenance tasks competently.
This afternoon, she slept for many hours... Which delighted and mystified us just a bit... then Noran realized... why
Cheese sandwiches, poop... for every thing, there is a season.
Recently, she had a bit of an output backlog. This is normal for infants of her age, but still managed to concern us, primarily via the lack of a sleep state that this caused. Our subsequent exhaustion then cause a ripple through our I/O as well.
We were relieved when her distress ceased, and the output queue was cleared. We had a visit with the diagnostician today, who monitors her functions and growth. She's progressing quite well, and we're performing our management and maintenance tasks competently.
This afternoon, she slept for many hours... Which delighted and mystified us just a bit... then Noran realized... why
She's all pooped out!
Cheese sandwiches, poop... for every thing, there is a season.
Tuesday, June 20, 2006
Tuesday, June 13, 2006
My identity stolen too.... 8(
It turns out I'm one of the 26 million veterans who had their information stolen. I'd be tempted to throw stones at the VA... but that's just reactionary diversion from the real problem.
Now... why is it that knowing my Name, Address, and SSN is enough to impersonate me?
...
...
Because the credit reporting agencies can't imagine a proper system of authentication (or just don't want to invest in one)...
I think it's absurd that a few digits of information are all that separate my credit history from oblivion. Why do we persist in blaming everyone except the credit companies for this problem?
There are better ways to authenticate people, we need to figure out what they are, and use them. The days of counting on a 10 to 20 digit number as ultimate security are over. Why should 26 million of us have our credit at the mercy of a single string of digits?
It's nuts... time to crack down on the real problem.... outmoded authentication systems.
--Mike--
Now... why is it that knowing my Name, Address, and SSN is enough to impersonate me?
...
...
Because the credit reporting agencies can't imagine a proper system of authentication (or just don't want to invest in one)...
I think it's absurd that a few digits of information are all that separate my credit history from oblivion. Why do we persist in blaming everyone except the credit companies for this problem?
There are better ways to authenticate people, we need to figure out what they are, and use them. The days of counting on a 10 to 20 digit number as ultimate security are over. Why should 26 million of us have our credit at the mercy of a single string of digits?
It's nuts... time to crack down on the real problem.... outmoded authentication systems.
--Mike--
Friday, June 09, 2006
How NOT to do identity
There's a thread over at the 37 signals blog that calls for the idea of portable credit card numbers. Its interesting that none of the comments so far see the inherent security issues with this idea.
Phone number portablity is nice because humans are expected to dial numbers, and it's very useful to associate a number with a person, and have the relationship persist for tens of years. There is no real security issue with this because the knowledge of a phone number has reasonably low value in scamming. The fact that numbers are considered permanent helps also keep the required size of the number pool smaller (new area codes not withstanding).
A credit card number happens to be its present size due to historical circumstances. Its an account number, from computers, for computers. The fact that a human may be required to recite it from time to time is the primary reason they aren't longer, or cryptographically secure (i.e. 1024+ bit random numbers in hex --> 256 characters long!)
Unlike phone numbers, the current credit card system relies on the 16 digit number as an essential element of security. Its part of a secret, along with a "security code" (3 or 4 digits tacked on to answer public concerns in the last few years), and the name, address, and other identifying (and likely publicly) data.
The current credit card system is amazingly insecure. The mere knowledge of a few facts, along with the 16+4 digits allows one to charge ANY AMOUNT against a credit card account, for the duration of the life of the card. The system forces the card holder to trust every merchant the wish to conduct business with, for the full security of this information. This is equivalent to handing all of you money to the merchant, and trusting they will take the correct amount of cash before returning your wallet to you. Only it's not even that safe, they can then dip into your wallet at any time in the future. If their computers are compromised, they anyone else who learns this secret aquires the same capablity.
A far more reasonable approach would be to use one time keys for every transaction. The credit card companies could offer a smart card, which would compute a cryptographically secure payment code which would denote the amount authorized, along with any authorization for future payments. The payment code would only work for the specified payee... if their computers were compromised, or if anyone else learned the secret... the knowledge would have zero value.
This is how this should be done. It's silly to trust that a 16 digit number with our financial futures.
Your credit card number is NOT an identity... don't be fooled into thinking it is.
--Mike--
Phone number portablity is nice because humans are expected to dial numbers, and it's very useful to associate a number with a person, and have the relationship persist for tens of years. There is no real security issue with this because the knowledge of a phone number has reasonably low value in scamming. The fact that numbers are considered permanent helps also keep the required size of the number pool smaller (new area codes not withstanding).
A credit card number happens to be its present size due to historical circumstances. Its an account number, from computers, for computers. The fact that a human may be required to recite it from time to time is the primary reason they aren't longer, or cryptographically secure (i.e. 1024+ bit random numbers in hex --> 256 characters long!)
Unlike phone numbers, the current credit card system relies on the 16 digit number as an essential element of security. Its part of a secret, along with a "security code" (3 or 4 digits tacked on to answer public concerns in the last few years), and the name, address, and other identifying (and likely publicly) data.
The current credit card system is amazingly insecure. The mere knowledge of a few facts, along with the 16+4 digits allows one to charge ANY AMOUNT against a credit card account, for the duration of the life of the card. The system forces the card holder to trust every merchant the wish to conduct business with, for the full security of this information. This is equivalent to handing all of you money to the merchant, and trusting they will take the correct amount of cash before returning your wallet to you. Only it's not even that safe, they can then dip into your wallet at any time in the future. If their computers are compromised, they anyone else who learns this secret aquires the same capablity.
A far more reasonable approach would be to use one time keys for every transaction. The credit card companies could offer a smart card, which would compute a cryptographically secure payment code which would denote the amount authorized, along with any authorization for future payments. The payment code would only work for the specified payee... if their computers were compromised, or if anyone else learned the secret... the knowledge would have zero value.
This is how this should be done. It's silly to trust that a 16 digit number with our financial futures.
Your credit card number is NOT an identity... don't be fooled into thinking it is.
--Mike--
Sunday, May 28, 2006
Finding balance
I'm spending a lot of energy trying to find balance today. With the arrival of our daughter, Virginia this week, everything has changed.
Getting the right amount of food, clothing and diapers for her is part of it. I'm finally comfortable changing diapers... a balance of preparation and improvisation is required.
I posted photos on Flickr... but didn't quite feel comfortable leaving them public. So I changed them to the "family and friends" setting... which makes me much more comfortable, but does tend to block off the serindiptious nature of Flickr.... so I still don't feel balanced.
I'm sure discussing all of this with friends and family will eventually help me reach a sane balance to all of these matters and more.
She's soooooo cute when she sleeps! (But I worry because she's so quiet!)
Well... she's waking up....
--Mike--
Getting the right amount of food, clothing and diapers for her is part of it. I'm finally comfortable changing diapers... a balance of preparation and improvisation is required.
I posted photos on Flickr... but didn't quite feel comfortable leaving them public. So I changed them to the "family and friends" setting... which makes me much more comfortable, but does tend to block off the serindiptious nature of Flickr.... so I still don't feel balanced.
I'm sure discussing all of this with friends and family will eventually help me reach a sane balance to all of these matters and more.
She's soooooo cute when she sleeps! (But I worry because she's so quiet!)
Well... she's waking up....
--Mike--
Saturday, May 27, 2006
Life
Children are a blessing from God.
They let us re-live and reflect on our own life, offering a more profound understanding and deeper sense of joy for all they encounter.
I'm a very lucky man.
They let us re-live and reflect on our own life, offering a more profound understanding and deeper sense of joy for all they encounter.
I'm a very lucky man.
Friday, May 19, 2006
Why we can't save the internet, yet
Doc has a thread going about saving the internet as we know it. His focus is on maintaining "net neutrality" or "net equality", and there's a lot of energy being thrown at this issue. Regardless of the lobbying efforts and the grass roots response... right now we just can't save the net.
Why?
Security
Having a fair and open internet requires that everyone have a nice wide open set of TCP and UDP ports... which is suicidal with today's operating systems. Everyone filters things behind firewalls and filters. Thus, the battle for an open net is effectively lost.
If anyone needs an excuse to defend their actions, they can simply assert "oh... we're just protecting the users"... and innovation dies a rapid death.
I've written so many times about the need for real security that I'm afraid everyone's going to think I'm a broken record... but it's crucial that we get an OS together that can run mobile code, have all its ports open, and still remain secure.
Linux, MacOS, Unix, and Windows all are completely incapable of running mobile code in any type of secure fashion. Until we get the paradigm shifted to one built around not trusting code, we're not going to be able to trust our computers... and thus we can't trust the net.
Security, Security, Security.....
Why?
Security
Having a fair and open internet requires that everyone have a nice wide open set of TCP and UDP ports... which is suicidal with today's operating systems. Everyone filters things behind firewalls and filters. Thus, the battle for an open net is effectively lost.
If anyone needs an excuse to defend their actions, they can simply assert "oh... we're just protecting the users"... and innovation dies a rapid death.
I've written so many times about the need for real security that I'm afraid everyone's going to think I'm a broken record... but it's crucial that we get an OS together that can run mobile code, have all its ports open, and still remain secure.
Linux, MacOS, Unix, and Windows all are completely incapable of running mobile code in any type of secure fashion. Until we get the paradigm shifted to one built around not trusting code, we're not going to be able to trust our computers... and thus we can't trust the net.
Security, Security, Security.....
Tuesday, May 16, 2006
Seen on the red line
This is your life
and it's ending
one minute at a time
It makes you think...
It's time to smell the flowers
and it's ending
one minute at a time
It makes you think...
It's time to smell the flowers
Saturday, May 13, 2006
It's the 4th amendment, Stupid!
So I'm reading the link from one of my favorite Propagandists, Matt Drudge... this story - "Spy Agency Watching Americans From Space" written by Katherine Shrader of AP. The subject is one of the many stories written to help spin the news (long suspected by many of us) that we're being spied upon by OUR own government.
First we get the feel good use of spy satellites to Support Our Troops:
Then we get to the sugar coated lie:
No, actually it's all about the 4th Amendment to our Constitution....
It's interesting that the article goes on with this statement
So... it's ok for them to look at our individual homes. We just need to trust them, and not worry about Judical oversight any more, right?
Gosh, I guess we really didn't need the 4th amendment, did we? It's just too inconvinient for them to worry about....
NUTS!
First we get the feel good use of spy satellites to Support Our Troops:
It set up mobile command centers that sprung out of the backs of Humvees and provided imagery for rescuers and hurricane victims who wanted to know the condition of their homes. Victims would provide their street address and the NGA would provide a satellite photo of their property. In one way or another, some 900 agency officials were involved.
Then we get to the sugar coated lie:
Spy agencies historically avoided domestic operations out of concern for Pentagon regulations and Reagan-era executive order, known as 12333, that restricted intelligence collection on American citizens and companies.
No, actually it's all about the 4th Amendment to our Constitution....
The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.See.... spying is the same as searching... and this is an attempt to justify unregulated searches... and nullify the 4th amendment, to allow spy agencies to operate domestically.
It's interesting that the article goes on with this statement
"We are not trying to examine an individual dwelling, for example, because what our mission is normally going to be is looking at large areas," he said. "It doesn't really affect or threaten anyone's privacy or civil liberties when you are looking at a large collective area."
So... it's ok for them to look at our individual homes. We just need to trust them, and not worry about Judical oversight any more, right?
Gosh, I guess we really didn't need the 4th amendment, did we? It's just too inconvinient for them to worry about....
NUTS!
Friday, May 12, 2006
Inventing the future
Alan Kay said it in 1971....
Computers can be secure, and much much faster. We shouldn't be forced to worry about little strings of digits controlling our financial future. We shouldn't be forced to import our energy. There are many things we can change, and make much better. It'll require effort, but it is possible. Join me in my quest to build a better future.
--Mike--
"Don't worry about what anybody else is going to do… The best way to predict the future is to invent it. Really smart people with reasonable funding can do just about anything that doesn't violate too many of Newton's Laws!"I've got quite a few ideas bouncing around in me... and I'm frustrated with my own inability to get them substantiated into reality. I'm hoping this blog will help change that. I seek others who want to discuss ideas and build the future. I don't care who profits, as long as I'm not left in the poor house.
Computers can be secure, and much much faster. We shouldn't be forced to worry about little strings of digits controlling our financial future. We shouldn't be forced to import our energy. There are many things we can change, and make much better. It'll require effort, but it is possible. Join me in my quest to build a better future.
--Mike--
Thursday, May 11, 2006
Stone age credit
Here we are in the year 2006, and we're still gullible enough to think the knowledge of a 16 digit number is enough to justify handing over money? ALL of someone's money? AND kill their future credit?
WTF?
What I want to know is why anyone still is being forced to use a system from the 1950s to handle their financial transactions in the world. The validation of credit cards is done online... why can't their be a pin number for face to face transactions, just like a debit card?
For online transactions, why can't we log into our issuing banks system, and generate a ONE TIME number for each and every separate transaction? We're already online... wouldn't it be worth a cut and paste to protect your financial reputation?
If the one time use numbers were tied to the recipient of the money, many of the woes that we consumers are faced to deal with would immediately disappear... compromise of one vendors database would be worth approximately $0.00 to any other vendor or customer.
Why doesn't this happen? People aren't aware of the technical possibilities, just as they don't know enough about DRM to seek open alternatives. We all need to find our voices, both online and elsewhere, and help bring the power of the technology we've built to everyone. Because we're not aware of the possiblities, we put up with utterly obsolete systems for moving money.
The same thing is true in many other intersections of technology and everyday life. There are models for computing security that are fast and secure, but not actively pursued. There are other computer architectures which may be able to offer a few orders of magnitude increase in computation speed for specialized tasks.
We need to talk about possibilites in the long term, as well as the short term. We need to get our imagination back. I've long known that some day I would be able to afford a Terabyte of disk space... and I imagine I'll buy it some time in the next 2 years. What the future holds in terms of computing is simply astounding.
We need to be aware of the forces that want to stop things for their own benefit, such as the Phone and Media companies. We need to creatively route around their economically motivated damage to innovation.
I fear that if we fail to do this, the enlightenment itself is going to be rolled back... and I definitely don't want that to happen.
--Mike--
WTF?
What I want to know is why anyone still is being forced to use a system from the 1950s to handle their financial transactions in the world. The validation of credit cards is done online... why can't their be a pin number for face to face transactions, just like a debit card?
For online transactions, why can't we log into our issuing banks system, and generate a ONE TIME number for each and every separate transaction? We're already online... wouldn't it be worth a cut and paste to protect your financial reputation?
If the one time use numbers were tied to the recipient of the money, many of the woes that we consumers are faced to deal with would immediately disappear... compromise of one vendors database would be worth approximately $0.00 to any other vendor or customer.
Why doesn't this happen? People aren't aware of the technical possibilities, just as they don't know enough about DRM to seek open alternatives. We all need to find our voices, both online and elsewhere, and help bring the power of the technology we've built to everyone. Because we're not aware of the possiblities, we put up with utterly obsolete systems for moving money.
The same thing is true in many other intersections of technology and everyday life. There are models for computing security that are fast and secure, but not actively pursued. There are other computer architectures which may be able to offer a few orders of magnitude increase in computation speed for specialized tasks.
We need to talk about possibilites in the long term, as well as the short term. We need to get our imagination back. I've long known that some day I would be able to afford a Terabyte of disk space... and I imagine I'll buy it some time in the next 2 years. What the future holds in terms of computing is simply astounding.
We need to be aware of the forces that want to stop things for their own benefit, such as the Phone and Media companies. We need to creatively route around their economically motivated damage to innovation.
I fear that if we fail to do this, the enlightenment itself is going to be rolled back... and I definitely don't want that to happen.
--Mike--
Wednesday, May 10, 2006
Still clueless about security
The /. community still hasn't figured out that they all live inside a box... if you want proof, just look at this recent discussion about security. Everyone pointing blame at the vendors, the users, and the criminals. The blame game can go on forever, and it'll never solve the problem.
The assumption built into almost everyone's world view is so well embedded it's almost impossible to see. Everyone assumes that there is a way to build a trustworthy computing system with today's OS models. It's patently absurd in my world view.
It's impossible to write code without bugs. Requiring the code to be perfect as a layer of security is insane. We should almost NEVER trust the code.
There should be one, and only one, piece of code on the planet that gets trusted... the kernel responsible for handling virtualization inside an OS. This code is irreplacable, all of the rest of it shouldn't be trusted.
Once we move past the blame game (if ever) and stop trusting the code, we'll be able to run anything from anywhere without fear.
--Mike--
- Blame the vendors - assumes that they can build a system worthy of trust
- Blame the users - assumes an paranoid user can be safe
- Blame the criminals - admit the problem is un-solveable
The assumption built into almost everyone's world view is so well embedded it's almost impossible to see. Everyone assumes that there is a way to build a trustworthy computing system with today's OS models. It's patently absurd in my world view.
It's impossible to write code without bugs. Requiring the code to be perfect as a layer of security is insane. We should almost NEVER trust the code.
There should be one, and only one, piece of code on the planet that gets trusted... the kernel responsible for handling virtualization inside an OS. This code is irreplacable, all of the rest of it shouldn't be trusted.
Once we move past the blame game (if ever) and stop trusting the code, we'll be able to run anything from anywhere without fear.
--Mike--
Linking 1 2 3
Steve Gillmor thinks that linking has been gamed to death, making it worse than useless. I see how he might get tired of seeing the same link in multiple places, but he's reading the situation with just a bit too much cynicism.
The links themselves haven't been gamed at all. The gaming comes when the links get decoupled from their ends, and aggregated. Technorati, Digg, Google, and all the others divorce the link from its context, which is how the opening for gaming got created.
If Steve, Doc, or someone else makes a link to a site, it can't get gamed between the author and the person directly reading the page (or RSS thereof). It's only in the value subtractive process of Silage that we open the door for rot (aka Gaming the system).
The point of Gesturebank seems to be to preserve the context, and try to avoid undifferentiated bulk accumulation of data, which is defintely the way forward. I'm still waiting to be able to see the data I'm already giving to the cause there... (I don't get to see the anonymous pile of data yet, for some reason) because I think it'll be VERY interesting, and useful.
I'd like to know what Doc reads, and be able to make it as cheap as possible for him to point out something interesting. I imagine what we really need is the thing that Vanevar Bush originally described back in 1945... a system for leaving a trail of hyperlinks and commentary about a vast collection of documents.
The threads are the value, not just the weight of them, or their bulk counts. We need to preserve the value of the ends by building and using tools which keep his in mind.
--Mike--
The links themselves haven't been gamed at all. The gaming comes when the links get decoupled from their ends, and aggregated. Technorati, Digg, Google, and all the others divorce the link from its context, which is how the opening for gaming got created.
If Steve, Doc, or someone else makes a link to a site, it can't get gamed between the author and the person directly reading the page (or RSS thereof). It's only in the value subtractive process of Silage that we open the door for rot (aka Gaming the system).
The point of Gesturebank seems to be to preserve the context, and try to avoid undifferentiated bulk accumulation of data, which is defintely the way forward. I'm still waiting to be able to see the data I'm already giving to the cause there... (I don't get to see the anonymous pile of data yet, for some reason) because I think it'll be VERY interesting, and useful.
I'd like to know what Doc reads, and be able to make it as cheap as possible for him to point out something interesting. I imagine what we really need is the thing that Vanevar Bush originally described back in 1945... a system for leaving a trail of hyperlinks and commentary about a vast collection of documents.
The threads are the value, not just the weight of them, or their bulk counts. We need to preserve the value of the ends by building and using tools which keep his in mind.
--Mike--
Friday, April 21, 2006
Spring
Saving Democracy
Doc talks about wanting to save the net, but I worried about the bigger picture. As I pointed out recently, I feel that Democracy is at stake. We've got a press thats been neutered, and a culture that only worries about quarterly results.
The stakes are bigger than the amount we're going to have to pay to download the White Album for the 10th time (along with the bonus DVD)... it's the very nature of our society that is truely at stake.
Doc thought part of it to be hyperbole when he mentioned Hal Crowther's article about the neutered press. I think we need to all collectively gather up our courage, and commit ourselves to doing a few simple things, with as much persistance as we possibly can:
Thanks for your time and attention.
--Mike--
The stakes are bigger than the amount we're going to have to pay to download the White Album for the 10th time (along with the bonus DVD)... it's the very nature of our society that is truely at stake.
Doc thought part of it to be hyperbole when he mentioned Hal Crowther's article about the neutered press. I think we need to all collectively gather up our courage, and commit ourselves to doing a few simple things, with as much persistance as we possibly can:
- Don't repeat the party line, don't feed the corporate propaganda machine with its insistence on topics de jure. Doc linked to a propaganda piece in The New Republic, and he was nice enough to link to my comment flagging it as such (as I'm composing this!)
- Don't just react, be proactive... think about the message you're sending... if all else fails, let the post sit overnight before posting it. (Breaking my own rules here.... hmmmm)
- Try to think in the biggest possible picture, but do what you can to make a difference that you can see (and measure). We need the ego gratification of getting something accomplished to help sustain our efforts.
- Speak up in person, as well as online. If someone says something you disagree with, please use your hard won right to express your view point, and who knows, you both might learn something.
- It's all about dialog... not just rants (which this may prove to be.... time will tell)
Thanks for your time and attention.
--Mike--
Tuesday, April 18, 2006
Desktop de jour
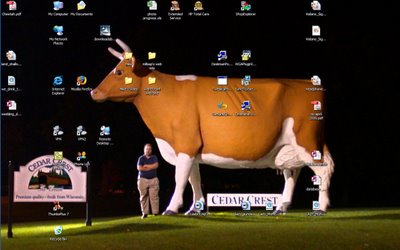
Since Dave posted his, I figured I might was well pile on.... here's a smaller version of my desktop.
I'm standing next to the giant cow in front of the Cedar Crest dairy in Manitowac, Wisconsin. It was part of a wonderful road trip with Noran.
I've got one of those "widescreen" laptops, so I've moved the task bar over to the left edge to save space. For the most part it works, but someone at Microsoft needs to use it like this for a few days to see where the quirks are, and get them fixed.
Failure of Imagination
It occured to me today that there is a massive failure of imagination taking place in the area of computer security these days. I see a world where you can run any program you please, without fear, on any ordinary computer.
I don't know of anyone else who shares this vision. I see myself as alone in a world of people who are trapped within the view that you just can't ever have a computer that is safe. I'm surrounded by people who are quite justifyably paranoid, based on the facts of their experience.
It doesn't have to be this way. I've got lots of things going on in my life, and it's about to get even busier... but I hope that one of the things I can do is to get rid of this pessimism and fear by helping to bring real security to computing.
Fear is a useful warning mechanisim in the sort term, but it makes you insane in the long run.
--Mike--
I don't know of anyone else who shares this vision. I see myself as alone in a world of people who are trapped within the view that you just can't ever have a computer that is safe. I'm surrounded by people who are quite justifyably paranoid, based on the facts of their experience.
It doesn't have to be this way. I've got lots of things going on in my life, and it's about to get even busier... but I hope that one of the things I can do is to get rid of this pessimism and fear by helping to bring real security to computing.
Fear is a useful warning mechanisim in the sort term, but it makes you insane in the long run.
--Mike--
Wednesday, April 12, 2006
Democracy - Broken
Here's the quote of the day from a posting at Daily Kos:
Totally independent of any spin from either side, I'd say this is the most accurate assessment of the state of our Union to date. It is imperative that we replace the mass media with real discussion and debate... Now!
--Mike--
Democracy as a government relies upon the ability of factions to compromise on divisive issues through rational debate instead of violence. The current political power brokers have figured out how to short circuit this process by focusing national attention on issues which are based on differences of non-negotiable, irrational moral sentiment, and are thus not subject to resolution through rational reconciliation. They've broken democracy.
Totally independent of any spin from either side, I'd say this is the most accurate assessment of the state of our Union to date. It is imperative that we replace the mass media with real discussion and debate... Now!
--Mike--
Thursday, April 06, 2006
New toy!
We got a spiffy new Ricoh copier today at work. It does 11x17 double sided color, and does it quickly. I managed to convert my April 2006 issue of CIO magazine into a 18 Megabyte PDF in about 2 minutes using the scanner (after removing the binding).
It's amazing how productive this new tool is going to make us.
8)
It's amazing how productive this new tool is going to make us.
8)
Still not secure
I said it before, I'll say it again... NO current PC operating system is secure, nor will any of them become secure.
Mac OSX, Windows and Linux will all succumb to virii, trojans and worms.
Looks like it just got a little worse for Windows, but don't worry ALL 3 will eventually get killed.
Any OS that trusts applications is doomed.
Mac OSX, Windows and Linux will all succumb to virii, trojans and worms.
Looks like it just got a little worse for Windows, but don't worry ALL 3 will eventually get killed.
Any OS that trusts applications is doomed.
Friday, March 31, 2006
Photo overload
I've got more digital photos than storage available on my laptop, so I'm having to do a purge. My current mode of operation is as follows:
The Kodak came from my friend Jim, who liked it, but didn't have the photography bug I had. It died after a solid year of service in a most inconvinent fashion, the backlight on the LCD died... the repairs were more than the cost of a replacement.
The Nikon 950 opened my eyes to the world of crystal clear photos, and macro photography. It's amazing how close this thing can focus to the lens. I've taken pictures of single drops of dew.
The Nikon 995 gave me more pixels, better controls, and a bit more flexibility.
The Nikon 5400 was even more pixels, but departed from the awesome macro, and wasn't quite what I expected. Noran loves it, so it's become her camera.
The Nikon 8800 is pretty darned good... it's got image stabilization and lots of features to go with the 8 megapixels. The only real disappointment has been the deliberatly non-stanard filter ring size, which makes the camera less flexible just so Nikon can sell a few more overpriced filters. (There are aftermarket ways around this, however)
As time goes on, I tend towards more photos per year... here's the trend:
It's going to be a very busy year, so I've got to get crackin' to get this done.
- use ThumbsPlus to do a slide show of all the images
- while viewing, alt-comma to tag the photos I want to save
- add the keyword Reviewed to the ones I've seen
- Control-Shift-V to invert the selection
- delete the photos I don't want to keep
- occasionally empty the recycle bin (helps keep the oops factor down)
- Casio QV-10 (320x240)
- Kodak DC210 (1152x864)
- Nikon Coolpix 950 (1600x1200)
- Nikon Coolpix 995 (2048x1536)
- Nikon Coolpix 5400 (2592x1944)
- Nikon Coolpix 8800 (3264x2448)
The Kodak came from my friend Jim, who liked it, but didn't have the photography bug I had. It died after a solid year of service in a most inconvinent fashion, the backlight on the LCD died... the repairs were more than the cost of a replacement.
The Nikon 950 opened my eyes to the world of crystal clear photos, and macro photography. It's amazing how close this thing can focus to the lens. I've taken pictures of single drops of dew.
The Nikon 995 gave me more pixels, better controls, and a bit more flexibility.
The Nikon 5400 was even more pixels, but departed from the awesome macro, and wasn't quite what I expected. Noran loves it, so it's become her camera.
The Nikon 8800 is pretty darned good... it's got image stabilization and lots of features to go with the 8 megapixels. The only real disappointment has been the deliberatly non-stanard filter ring size, which makes the camera less flexible just so Nikon can sell a few more overpriced filters. (There are aftermarket ways around this, however)
As time goes on, I tend towards more photos per year... here's the trend:
- 1997 - 198
- 1998 - 1768
- 1999 - 4223
- 2000 - 9941 (still in review)
- 2001 - 17,192
- 2002 - 26,065
- 2003 - 23,935
- 2004 - 17,704
- 2005 - not on laptop yet
- 2006 - 557
It's going to be a very busy year, so I've got to get crackin' to get this done.
Wednesday, March 29, 2006
ACT 2000 support sucks!
So, you install ACT 2000, and the first thing that happens is that the program has a bug that prevents it from seeing a working internet connection.
You get a dialog box that says:
What got me pissed is that when... you do a google search (on the computer in question) the first pair of solutions found (on their web site) are BOTH BROKEN.
DELIBERATELY
BY MARKETERS!
Sheesh... it's bad enough that it's not a real database, and the performance of the program sucks when you get past 10,000 records because of this, but do they have to cripple the only lifeline to us who have to deal with this thing?
Get a clue, ACT!
...
Even Microsoft has this one right... you don't have to sign up for anything to get support from their knowledgebase. It's one of the main things keeping system administrators like myself happy, or at least tollerant. We might not like them, but at least we can work with them.
--Mike--
You get a dialog box that says:
Internet connection required to check for updates could not be made.
In the Windows Control Panel, check the Internet Options
Dial-up Settings, or connect to the Internet and try again.
What got me pissed is that when... you do a google search (on the computer in question) the first pair of solutions found (on their web site) are BOTH BROKEN.
DELIBERATELY
BY MARKETERS!
Sheesh... it's bad enough that it's not a real database, and the performance of the program sucks when you get past 10,000 records because of this, but do they have to cripple the only lifeline to us who have to deal with this thing?
Get a clue, ACT!
...
Even Microsoft has this one right... you don't have to sign up for anything to get support from their knowledgebase. It's one of the main things keeping system administrators like myself happy, or at least tollerant. We might not like them, but at least we can work with them.
--Mike--
Tuesday, March 28, 2006
DRM
Dave thinks DRM is no big deal. For him, at this time, he's right. The music works, and he's happy.
I think he'll change his mind when he gets a newer computer, and the music doesn't move with his other stuff, or any of the other myriad ways that DRM truely messes with the transparency and utility of general purpose computation.
You'll eventually start worrying about DRM, Dave.... you're just young and innocent right now.
--Mike--
I think he'll change his mind when he gets a newer computer, and the music doesn't move with his other stuff, or any of the other myriad ways that DRM truely messes with the transparency and utility of general purpose computation.
You'll eventually start worrying about DRM, Dave.... you're just young and innocent right now.
--Mike--
Context
The context of something is important. In any story, there are the basic things to know:
Bill Clinton tried to use parsing to get his way out of an embarassing situation, and it backfired, big time. As a result we got our current administration... and I think we're all learning a painful lesson as a society as a result. Context is all important, word games don't cut it any more.
When appearances are all that matters, and there is no real attention being spent, you can get away with such matters. Once actual attention is being expended, lies and deceptions tend to dissolve into transparency. A mis-statement becomes far less damaging if actual human attention is involved in putting it all into context.
It is my belief that the whole web 2.0 thing is all about cutting through the crap, and actually paying attention to each other, and to things that really matter.
What you say may inconvinence you from now on, but it's not going to be the albitross it used to be. If you deal with it fairly in your blog, and keep the conversation about it open and honest and persistent, you can pretty much dig yourself out of any hole, no matter how big.
I'd be willing to bet that even Dan Quayle could get himself back into the public sphere as a viable candidate for President, if he blogged, and showed an open and intelligent side.
It's all about the context. Thank you for spending some of your time and attention reading this.
--Mike--
- who
- what
- where
- when
- why
Bill Clinton tried to use parsing to get his way out of an embarassing situation, and it backfired, big time. As a result we got our current administration... and I think we're all learning a painful lesson as a society as a result. Context is all important, word games don't cut it any more.
When appearances are all that matters, and there is no real attention being spent, you can get away with such matters. Once actual attention is being expended, lies and deceptions tend to dissolve into transparency. A mis-statement becomes far less damaging if actual human attention is involved in putting it all into context.
It is my belief that the whole web 2.0 thing is all about cutting through the crap, and actually paying attention to each other, and to things that really matter.
What you say may inconvinence you from now on, but it's not going to be the albitross it used to be. If you deal with it fairly in your blog, and keep the conversation about it open and honest and persistent, you can pretty much dig yourself out of any hole, no matter how big.
I'd be willing to bet that even Dan Quayle could get himself back into the public sphere as a viable candidate for President, if he blogged, and showed an open and intelligent side.
It's all about the context. Thank you for spending some of your time and attention reading this.
--Mike--
Saturday, March 25, 2006
Re-tuning the loop
Since writing about tuning the loop, I've decided that I've been reading and listening to too much hype, too many activists, too much stuff that turns out not to be true. Over time all things become transparent, and the hidden agendas and reactionary biases all show up. I've noticed way too much of stuff I've been reading turns out to be wrong.
I'm going to try to focus more on durable things, more substance, less flash.
--Mike--
I'm going to try to focus more on durable things, more substance, less flash.
--Mike--
Wednesday, March 15, 2006
Beware the Jumbo Frame
Never, EVER turn on "Jumbo Frames" on a Linksys SRW2048 switch.
Something overflows in the firmware, and things get very screwed up, very quickly.
Lost a few hours work for EVERYONE because of this. 8(
Update: January 10, 2008 - As noted in the comment below, I should have added more info. I've since learned that turning on Jumbo Frames is NOT a plug and play operation... ALL of the devices that might see a jumbo frame need to be able to handle them, or they will go off line.
Something overflows in the firmware, and things get very screwed up, very quickly.
Lost a few hours work for EVERYONE because of this. 8(
Update: January 10, 2008 - As noted in the comment below, I should have added more info. I've since learned that turning on Jumbo Frames is NOT a plug and play operation... ALL of the devices that might see a jumbo frame need to be able to handle them, or they will go off line.
Monday, March 13, 2006
America the Dis-functional
This is exactly where we're headed in our country without leadership.
The ME ME party has had power for too long... and the whiplash is about to hit.
Not a good place to be.
--Mike--
The ME ME party has had power for too long... and the whiplash is about to hit.
Not a good place to be.
--Mike--
Saturday, March 11, 2006
Myspace and Transparency
I'm going to remix three views of Myspace. The first is from USA Today, entitled "What you say online could haunt you". The second is a set of notes from a talk given by Danah Boyd. The last is my own.
USA today is basically a warning that the Myspace is visible to others. The stories were about kids who thought they could freely post private comments which were in conflict with their public persona. They share then common attribute of a mistaken believe that the system was private, or somehow obscured from view of those in public.
Danah talks about three spaces, Public, Private, and Controlled.
The kids all thought they were in a private space. It turned out that the schools and other authorities managed to extend the controlled space of their lives into MySpace. It's especially ironic given the name of the site.
The surprise at being called out on one's hyprocrisy and the pain that can result aren't pleasant. Some will grow from this experience, and the others will simply find or build a more private space.
We face similar societal learning in many other spheres of life. The sharing of MP3s is a social act, which initially via Napster had a postitive overall impact for everyone. The sales of CDs got a shot in the arm, and a lot of people got to hear new artists and learn more about music. It was a public space.
The RIAA managed to change Napster from a Public to a Controlled space. Their actions shifted from trying to seek the copyright protections expressed in The Constitution, into a witchhunt.
The loss of Napster as a space to share copyrighted content freely was accepted by many, including myself. Not satisifed with cutting their own throats, the RIAA has been joined by MPAA and turned it into a crusade against any type of electronic file distribution.
There are many reasons to want to distribute a file, the RIAA and MPAA do it all the time, but they have monopolies on non-electronic distribution, so it's easy to see the motivation here.
The bought-off Congress has pushed through ill considered legislation which has further pushed along the anti-distribution crusade, which is starting to look like a war on the internet.
Eventually this will all come to bite back in one kharmic retribution. Why? It reduces transparency of the internet by encouraging encryption of traffic. This will make it increasingly hard for the NSA and others to gather intellegence. In one fell swoop, the crusade has managed to counteract untold (classified) amounts of investment in electronic espionage and monitoring systems.
---
The right to privacy isn't in the Constitution, it wasn't necessary before the communications revolutions of telegraph, telephone, radio and internet. The current climate isn't going to allow it to be amended to the constitution.
The right to find others in pursuit of building a private space, however is readily apparent. The boundaries of society are shifting, as they always have. The countermeasures against monitoring and social control will be adopted, and this will just become one more chapter in an endless story.
Over time even lies become become transparent.
Thank you for your time and attention.
--Mike--
USA today is basically a warning that the Myspace is visible to others. The stories were about kids who thought they could freely post private comments which were in conflict with their public persona. They share then common attribute of a mistaken believe that the system was private, or somehow obscured from view of those in public.
Danah talks about three spaces, Public, Private, and Controlled.
The kids all thought they were in a private space. It turned out that the schools and other authorities managed to extend the controlled space of their lives into MySpace. It's especially ironic given the name of the site.
The surprise at being called out on one's hyprocrisy and the pain that can result aren't pleasant. Some will grow from this experience, and the others will simply find or build a more private space.
We face similar societal learning in many other spheres of life. The sharing of MP3s is a social act, which initially via Napster had a postitive overall impact for everyone. The sales of CDs got a shot in the arm, and a lot of people got to hear new artists and learn more about music. It was a public space.
The RIAA managed to change Napster from a Public to a Controlled space. Their actions shifted from trying to seek the copyright protections expressed in The Constitution, into a witchhunt.
The loss of Napster as a space to share copyrighted content freely was accepted by many, including myself. Not satisifed with cutting their own throats, the RIAA has been joined by MPAA and turned it into a crusade against any type of electronic file distribution.
There are many reasons to want to distribute a file, the RIAA and MPAA do it all the time, but they have monopolies on non-electronic distribution, so it's easy to see the motivation here.
The bought-off Congress has pushed through ill considered legislation which has further pushed along the anti-distribution crusade, which is starting to look like a war on the internet.
Eventually this will all come to bite back in one kharmic retribution. Why? It reduces transparency of the internet by encouraging encryption of traffic. This will make it increasingly hard for the NSA and others to gather intellegence. In one fell swoop, the crusade has managed to counteract untold (classified) amounts of investment in electronic espionage and monitoring systems.
---
The right to privacy isn't in the Constitution, it wasn't necessary before the communications revolutions of telegraph, telephone, radio and internet. The current climate isn't going to allow it to be amended to the constitution.
The right to find others in pursuit of building a private space, however is readily apparent. The boundaries of society are shifting, as they always have. The countermeasures against monitoring and social control will be adopted, and this will just become one more chapter in an endless story.
Over time even lies become become transparent.
Thank you for your time and attention.
--Mike--
Tuesday, March 07, 2006
 It's time to get rid of the stuff I've been saving "just in case". Spring cleaning is a ritual I've skipped for most of my life, preferring instead the "safety" of having things I might need some day. It's a false sense of security, and I've realized the costs are far higher than I had imagined. It's very liberating to get rid of 50 pounds of cables and old mice, etc.
It's time to get rid of the stuff I've been saving "just in case". Spring cleaning is a ritual I've skipped for most of my life, preferring instead the "safety" of having things I might need some day. It's a false sense of security, and I've realized the costs are far higher than I had imagined. It's very liberating to get rid of 50 pounds of cables and old mice, etc.It all started when I saw a picture of my office, and the most visible object was the mess. I'm taking the advice I've been given many times, getting rid of the most visually obvious stuff first, to get some momentum going.
I look forward to the changes ahead in my life, and with a glad heart look forward to the work required to bring them about.
--Mike--
Monday, March 06, 2006
The Importance of Good Tools
I kept LaptopJenny the HP ZE4430US going as long as I could. The inevitable demise last week marked an end of a series of struggles that had HP on my shit list, until I got a look inside, and saw just how much she really had been through. That changed my mind.
In looking for a new laptop, I had a few criteria:
It's like being able to breath again... I've got a tool I can use to create or recreate. It plays Civ4 in real time, without stutter or any delay. It's almost flawless in going through the intro movie... just amazing!
Having good tools gives you so much more capability than merely settling for adequate. I've got more than sufficient power and speed to do what I want. I don't have to find the one seat on the train near an outlet any more. Ahhh, the true taste of freedom!
A surprise over the weekend was the truly massive extent of my digital photo collection. I've got something like 120 Gigabytes of photos! I thought it was more like 45 Gb... Which means I really have to buckle down and prune.
I'll be putting some of them up in my Flickr account that I feel are suitable for the public. I'll be using ThumbsPlus 7 from Cerious to keep them organized, and allow fast keyword searches.
WoW, it's soooo good to have good tools!
I'm free!
In looking for a new laptop, I had a few criteria:
- 1 GB RAM (or more)
- SEPARATE Video RAM
- BRIGHT display
- Dual Layer DVD burner
- WiFi G
- Don't settle
It's like being able to breath again... I've got a tool I can use to create or recreate. It plays Civ4 in real time, without stutter or any delay. It's almost flawless in going through the intro movie... just amazing!
Having good tools gives you so much more capability than merely settling for adequate. I've got more than sufficient power and speed to do what I want. I don't have to find the one seat on the train near an outlet any more. Ahhh, the true taste of freedom!
A surprise over the weekend was the truly massive extent of my digital photo collection. I've got something like 120 Gigabytes of photos! I thought it was more like 45 Gb... Which means I really have to buckle down and prune.
I'll be putting some of them up in my Flickr account that I feel are suitable for the public. I'll be using ThumbsPlus 7 from Cerious to keep them organized, and allow fast keyword searches.
WoW, it's soooo good to have good tools!
I'm free!
Sunday, March 05, 2006
Ahhhhhh....
It's a lazy sunday, with the warm caress of my lovely and caring wife, no schedules, no deadlines... just relaxation...
ahhhh
ahhhh
3rd party markup!
Doc wonders about getting a snarkiness slider in Technorati. Well it would be useful if we could tag snarky stuff.
WE tag STUFF
3rd Party markup is what's missing here... WE can't tag anything... the author does, which means it's not going to be an accurate measurement of the nature of the content. Embedded tagging makes spamming easy, and hard to reverse.
We need 3rd party markup!
WE tag STUFF
3rd Party markup is what's missing here... WE can't tag anything... the author does, which means it's not going to be an accurate measurement of the nature of the content. Embedded tagging makes spamming easy, and hard to reverse.
We need 3rd party markup!
Thursday, March 02, 2006
Podcasts need sponsors?
The whole point of podcasting seems to be to let a few guys have an interesting conversation in front of a reasonable recording system. From the few I've listened to, there seems to be no interest in cleaning up the audio, or even bothering to get a decent quality connection in some cases. Low quality phone connections seem to me to be part of the "charm" of podcasting.
I'm learning that a good blog entry has to be edited. Why can't the podcasters take the time to clean up the audio a bit?
If you're not going to be bothered to turn out a professional quality product, you've not sunk any costs. What qualifies the podcast for the value subtraction inherent in an AD? If you're not willing to add value to a few guys talking... you essentially lower the value back towards zero.
We're all supposed to ADD value to the blogosphere. Communism? Perhaps, but it's the community values we seem to share. Let's keep it that way.
It doesn't cost anything to do a digital sound recording. It costs little to do it right. Someone with a good ear for editing could clean things up. You can keep the dollar cost to zero, and avoid sponsorship.
To prove the point... here's an MP3 I made on a laptop, (349kb, 50 seconds) with the most basic software imaginable, Sound Recorder in Windows XP. Consider it my very first podcast, if you like. Here's my transcript (notably missing from most podcasts)
I found a cost... you need to have a host for your MP3 file... I happen to use 1and1 to host the family domain, so it's a sunk cost for me. I doubt this file will put me anywhere near my bandwidth cap. If it did, then it would be encrypted bittorrent time.
The biggest cost so far is the time to do the transcript, which is about 6 times the length of the recording. It's tempting to go back and edit out some pauses, etc.
I'm willing to give the benefit of the doubt... what are the costs associated with doing a podcast?
I'm learning that a good blog entry has to be edited. Why can't the podcasters take the time to clean up the audio a bit?
If you're not going to be bothered to turn out a professional quality product, you've not sunk any costs. What qualifies the podcast for the value subtraction inherent in an AD? If you're not willing to add value to a few guys talking... you essentially lower the value back towards zero.
We're all supposed to ADD value to the blogosphere. Communism? Perhaps, but it's the community values we seem to share. Let's keep it that way.
It doesn't cost anything to do a digital sound recording. It costs little to do it right. Someone with a good ear for editing could clean things up. You can keep the dollar cost to zero, and avoid sponsorship.
To prove the point... here's an MP3 I made on a laptop, (349kb, 50 seconds) with the most basic software imaginable, Sound Recorder in Windows XP. Consider it my very first podcast, if you like. Here's my transcript (notably missing from most podcasts)
So, my question is...
since anybody can record a digital sound file for essentially no money,
and for tech guys should be able to do it for no money,
why do they need sponsors?
why does anybody need to be paid
to record something and record it to a file
and put it on a server
and let people download it
where's the money going
why does any sponsorship need to be there?
you don't have to pay to promote it
you really don't have to pay to produce it
doesn't make sense
that's it.
I found a cost... you need to have a host for your MP3 file... I happen to use 1and1 to host the family domain, so it's a sunk cost for me. I doubt this file will put me anywhere near my bandwidth cap. If it did, then it would be encrypted bittorrent time.
The biggest cost so far is the time to do the transcript, which is about 6 times the length of the recording. It's tempting to go back and edit out some pauses, etc.
I'm willing to give the benefit of the doubt... what are the costs associated with doing a podcast?
One dead laptop, Free HP ZE4430US parts
The laptop had a non-zif CPU socket... broke it trying to get the CPU secured. Jenny is dead, and now becomes a laptop organ donor.
--
Now that I'm over the anger at myself... I offer the following parts for free to a good home:
From an HP ZE4430US laptop
Leave a comment if you can use any of this. I'll remove items as they get spoke for.
--
Now that I'm over the anger at myself... I offer the following parts for free to a good home:
From an HP ZE4430US laptop
- Top half, including Display -1024x768, active matrix
- Interal WiFi G card, and the cables and antennae, and the little on/off switch and hardware
- 2x256 MB RAM
- CD-RW/DVD drive, with latest firmware
- Keyboard
Leave a comment if you can use any of this. I'll remove items as they get spoke for.
Wednesday, March 01, 2006
Parts is Parts
I just got done taking my laptop completely apart. It is (and should be again) an HP Pavilion 4430US. It's got power connector issues, and I found a bit of corrosion on a corner of the motherboard... fortunately it looks isolated to that one area, I wonder what got spilled in there.
I removed everything I could, RAM, WiFi board, PCMCIA slot, even the CPU, as many stickers etc, ... and especially the rechargable CMOS battery.
I took it to the sink, and washed it with soap and water. I rinsed it, TWICE.
Now to let it air dry overnight. I'll inspect the power connector circuitry more closely in the morning, and see if it looks like anything is wrong. Repair if necessary, then re-assembly.
Didn't want to do it, but them's the breaks. Can't afford to just throw it out without at least making a serious repair effort.
Parts is parts... I'm hoping it'll once again be more than the sum of its parts tomorrow.
--Mike--
I removed everything I could, RAM, WiFi board, PCMCIA slot, even the CPU, as many stickers etc, ... and especially the rechargable CMOS battery.
I took it to the sink, and washed it with soap and water. I rinsed it, TWICE.
Now to let it air dry overnight. I'll inspect the power connector circuitry more closely in the morning, and see if it looks like anything is wrong. Repair if necessary, then re-assembly.
Didn't want to do it, but them's the breaks. Can't afford to just throw it out without at least making a serious repair effort.
Parts is parts... I'm hoping it'll once again be more than the sum of its parts tomorrow.
--Mike--
Tuesday, February 28, 2006
Technorati musings - part 3
Technorati tags are an interesting idea, but it falls apart under real world conditions.
Embedded Tagging Only
Because the author of a blog is the only one who can inject tags, this presents a wide open opprotunity for spammers to turn Technorati into a spam search engine - a spamgine? See Om Malik's post for more details.
The author of the post is unlikely to search and find all applicable blogs, as they just want to get the post written. Thus it's unlikely to ever become a majority action.
Tags are vague
Since any arbitrary word can get used as a tag, the probability is that the need for disambiguation will overwhelm their utility. Coupled with the lack of the AND operator at technorati, this becomes a fatal flaw in itself.
No markup tags
The author of a post is probably the last one you want to criticize the post, which is where tagging can be its most powerful. If the rest of us could tag posts, it would be far more likely to be an accurate (or somewhat fair) representation of what a post was really about. Even a popularity contest is going to be more representative than self nomination and promotion.
Embedded Tagging Only
Because the author of a blog is the only one who can inject tags, this presents a wide open opprotunity for spammers to turn Technorati into a spam search engine - a spamgine? See Om Malik's post for more details.
The author of the post is unlikely to search and find all applicable blogs, as they just want to get the post written. Thus it's unlikely to ever become a majority action.
Tags are vague
Since any arbitrary word can get used as a tag, the probability is that the need for disambiguation will overwhelm their utility. Coupled with the lack of the AND operator at technorati, this becomes a fatal flaw in itself.
No markup tags
The author of a post is probably the last one you want to criticize the post, which is where tagging can be its most powerful. If the rest of us could tag posts, it would be far more likely to be an accurate (or somewhat fair) representation of what a post was really about. Even a popularity contest is going to be more representative than self nomination and promotion.
Hyperwords and Collaboration
Collaboration: 1970s
When I went to school, we had a model of collaboration based on an old technology, paper. We started with an existing document, and added information to it. This would transform the document from let's say a piece of ruled paper, into an essay. Or in other cases it would transform a quiz or test into our completed sheet, which would then be forwarded for further processing.
The teacher would then read the document, circle or highlight, or otherwise add markup and notations to help indicate areas of improvement, correction, or other information. The document would then be sent back to the student to complete the feedback loop.
It was a simple, effective workflow, with millenia of experience embedded into it.
Collaboration: Web 2.0
Create a document in your editor of choice. Cut and paste and markup and highlight your text to suit your audience. Publish this document in HTML to a web server.
Since HTML doesn't allow external markup, the choices for your collaborators become:
The ability to add markup to a document is one of the key things that prevents Web 2.0 from really being a "live web". We can plaster our servers with pages, but no true markup is possible. The words on web pages are always always static, because they've been published.
HyperWords
Doc Searls solicited comments about the HyperWords plugin. With the above view of what it really takes to interact with a document, and the words within... I'd have to say it doesn't fit the bill. This plugin, though clever, and apparently a great tool, does nothing to change the read-only nature of the web (even the "Live Web").
I'm already using "search google for" in Firefox (highlight text, then right-click) as a very powerful cross referencing tool. The problem is that the cross reference doesn't persist. There's no permanent connection made between the document and the found links. In fact, there's no way to make any persistent markup of a web page in a browser. The browser is read-only, and is likely to remain that way for the duration.
Towards a writeable web
We do need the ability to make this stuff interactive. If I see something wrong with a posting, I should be able to put a post-it note up there, somehow. Even if nobody else can see it, it might be helpful for me. I believe that this markup of hypertext would be a quite valueable tool for others as well.
Any tool which helps transform the web from read-only to truely read-write in a sane process gets my vote.
I'm a hacker at heart, I'm willing to discuss the mechanics of this with anyone.
Notes:
Yes, I know that inviting markup invites grafitti, spam, etc. That's what IDENTITY is for, to help limit those the application of markup to those with non-bad (or perhaps good) reputations.
Yes, I know it'll require a new protocol to support annotation of external documents. HTML is embedded only, we need to rethink this.
I'm one lone voice in the wilderness, trying to find others who share my viewpoint. Can the live web help?
--Mike--
Technorati tag: hyperwords
When I went to school, we had a model of collaboration based on an old technology, paper. We started with an existing document, and added information to it. This would transform the document from let's say a piece of ruled paper, into an essay. Or in other cases it would transform a quiz or test into our completed sheet, which would then be forwarded for further processing.
The teacher would then read the document, circle or highlight, or otherwise add markup and notations to help indicate areas of improvement, correction, or other information. The document would then be sent back to the student to complete the feedback loop.
It was a simple, effective workflow, with millenia of experience embedded into it.
Collaboration: Web 2.0
Create a document in your editor of choice. Cut and paste and markup and highlight your text to suit your audience. Publish this document in HTML to a web server.
Since HTML doesn't allow external markup, the choices for your collaborators become:
- Copy the document, and embed markup in the document
- Point to the document you want to talk about, copying sections to try to bring focus to the areas of interest
- Point ot the document, and just write about it in general terms.
The ability to add markup to a document is one of the key things that prevents Web 2.0 from really being a "live web". We can plaster our servers with pages, but no true markup is possible. The words on web pages are always always static, because they've been published.
HyperWords
Doc Searls solicited comments about the HyperWords plugin. With the above view of what it really takes to interact with a document, and the words within... I'd have to say it doesn't fit the bill. This plugin, though clever, and apparently a great tool, does nothing to change the read-only nature of the web (even the "Live Web").
I'm already using "search google for" in Firefox (highlight text, then right-click) as a very powerful cross referencing tool. The problem is that the cross reference doesn't persist. There's no permanent connection made between the document and the found links. In fact, there's no way to make any persistent markup of a web page in a browser. The browser is read-only, and is likely to remain that way for the duration.
Towards a writeable web
We do need the ability to make this stuff interactive. If I see something wrong with a posting, I should be able to put a post-it note up there, somehow. Even if nobody else can see it, it might be helpful for me. I believe that this markup of hypertext would be a quite valueable tool for others as well.
Any tool which helps transform the web from read-only to truely read-write in a sane process gets my vote.
I'm a hacker at heart, I'm willing to discuss the mechanics of this with anyone.
Notes:
Yes, I know that inviting markup invites grafitti, spam, etc. That's what IDENTITY is for, to help limit those the application of markup to those with non-bad (or perhaps good) reputations.
Yes, I know it'll require a new protocol to support annotation of external documents. HTML is embedded only, we need to rethink this.
I'm one lone voice in the wilderness, trying to find others who share my viewpoint. Can the live web help?
--Mike--
Technorati tag: hyperwords
Sunday, February 26, 2006
Embedded Keywords
We're straddled with few ways of navigating the world wide web. Google and its kin are all based on the concept of keyword searches to dig through massive databases retrieved by spidering.
The interface we're given to try to mine this data is a keyword search, with modifiers. This is great if you're looking for the most popular use of a word, but if you're looking for the unpopular, you're screwed.
People tend to use the words they already seen used to describe a concept or viewpoint, or meme. Over time, because of our heavy use of keyword searches, the meme tends to monopolize certain keywords. This leads to the exclusion of other memes that discuss the same subject.
Keyword search then tends to result in an echo chamber, where a majority viewpoint gets found first, and much more frequently. It's a popularity contest if you will, for ownership of the keywords.
Language gets used as a tool of thought control if you think about it long enough. If you can invent a neologism, and maintain control over it's definition, you've just bought part of the language... now that's power!
There are alternatives, conversation unmediated by machine is the best. If you give authority to the machine, you end up thinking like one. Do not go gentle into that good night.
The interface we're given to try to mine this data is a keyword search, with modifiers. This is great if you're looking for the most popular use of a word, but if you're looking for the unpopular, you're screwed.
People tend to use the words they already seen used to describe a concept or viewpoint, or meme. Over time, because of our heavy use of keyword searches, the meme tends to monopolize certain keywords. This leads to the exclusion of other memes that discuss the same subject.
Keyword search then tends to result in an echo chamber, where a majority viewpoint gets found first, and much more frequently. It's a popularity contest if you will, for ownership of the keywords.
Language gets used as a tool of thought control if you think about it long enough. If you can invent a neologism, and maintain control over it's definition, you've just bought part of the language... now that's power!
keywords embedded in meme,
expressing the very same theme,
working together
through google and others,
framing the limits of dreams
There are alternatives, conversation unmediated by machine is the best. If you give authority to the machine, you end up thinking like one. Do not go gentle into that good night.
HTML - The Embedded Cancer
HTML is a great acronym if you like great lawyer speak. It's a term which has now monopolized the concept of markup, and is a cancer!
HTML is an EMBEDDED markup language. This means that the markup has to be intermixed with the text it is meant to mark up. This direct physical linkage, embedding, of the markup is great of you happen to be the owner of the document, and have the tools to hide the complexity of it's internal representation, but for everyone else, it's hell.
What HTML should been, is a markup language for hypertext. It should allow the markup of an existing SEPARATE document, by reference. Ted Nelson tried very hard to get this idea across to the masses, but when the critical moment came, Tim Berners Lee took the easy way out, and we're all screwed, even though most of us don't even know it.
There are a great many things that are broken as a result of this singularly bad choice. We're forced to rely on spiders to find documents on the world wide web. We have no ability to add commentary directly on top of other people's work, except by extraordinary measures, which break copyright rules.
The embedded nature of HTML has limited our range of thought. It is an example of how the limitations of language impose limitations of range of thought. If you can't imagine being able to highlight a section of someone's blog posting in yellow, with a hyperlink to something else, and a note that says something about the connection, you won't ever miss it.
HTML is evil. I'm open to any discussion about alternatives.
HTML is an EMBEDDED markup language. This means that the markup has to be intermixed with the text it is meant to mark up. This direct physical linkage, embedding, of the markup is great of you happen to be the owner of the document, and have the tools to hide the complexity of it's internal representation, but for everyone else, it's hell.
What HTML should been, is a markup language for hypertext. It should allow the markup of an existing SEPARATE document, by reference. Ted Nelson tried very hard to get this idea across to the masses, but when the critical moment came, Tim Berners Lee took the easy way out, and we're all screwed, even though most of us don't even know it.
There are a great many things that are broken as a result of this singularly bad choice. We're forced to rely on spiders to find documents on the world wide web. We have no ability to add commentary directly on top of other people's work, except by extraordinary measures, which break copyright rules.
The embedded nature of HTML has limited our range of thought. It is an example of how the limitations of language impose limitations of range of thought. If you can't imagine being able to highlight a section of someone's blog posting in yellow, with a hyperlink to something else, and a note that says something about the connection, you won't ever miss it.
HTML is evil. I'm open to any discussion about alternatives.
Discontent
I'm pissed about a number of things, mostly my own ability to articulate things, aided and abetted by the persistent doubt of actually making a difference anyway.
I'm going to make a series of posts, one per subject, so that if actual discussion follows... it won't be muddled up.
I'm going to make a series of posts, one per subject, so that if actual discussion follows... it won't be muddled up.
Friday, February 24, 2006
Clue train, redux
As pointed to a few days ago, over at Head Lemur's: Raving Lunacy, Marketing is a Disease
Wow! This has the barbaric yalp written all over it, and it's all dead true!
Good stuff, part of my daily reads.
--Mike--
Marketeers talk about control and spin. Traditional Marketing Wisdom stated that a bad customer experience would only lose you 7 customers. That was in the days of Monologue. This is age of Dialogue. The Internet and Blogs can cost you all of them. This is age of Dialogue. Genuine Dialogue. Every company who has tried ghost blogs has had their asses handed to them. We are smart and getting smarter every day. Our bullshit detectors will ferret you out and thousands of voices will point and laugh. You cannot spin your way out of this.
Wow! This has the barbaric yalp written all over it, and it's all dead true!
Good stuff, part of my daily reads.
--Mike--
"no-feedback" nonsense
I saw this diagram on this page found via Digg, which is a pretty good source of fresh new stuff to read about. I wanted to read about the big subwoofers... which are good to gawk at.
The part that gets in my craw is the misunderstanding of feedback.
The quote that goes with it the diagram contains an error
FIGURE BELOW: shows the Electromotive Energy produced by the speaker that thru the F.B. path reaches even your turntable cartridge. Amp and preamp are shown as Operational Amplifier for semplicity. Any linear amplifier is by definition an Operational amplifier with linear trasfer function used as a constant multiplier.There is a hidden assumption, left unwritten. This is that the transfer function is a constant multiplier in both directions. It's not true. The forward transfer function is almost perfectly a constant gain (multiplier), but the reverse function isn't.
The amplifier uses a low impedance output to supply whatever current is necessary to the load, with the feedback resistor along for the ride. The result is that any possible contribution to the current through the feedback resistor is shunted through the output stage to ground. This means that even a single stage amplifier will provide attenuations on order of Rout/Rfeedback * Open Loop Gain. This means that even a single stage is sufficient to completely isolate an input.
The insistance on "no-feedback" amplification makes for a nice market niche, but is not based on fact.
--Mike--
Thursday, February 23, 2006
The need for editing
Scott Adams discusses blogging in the form of a list of class notes. The one that caught my eye was
I respectfully disagree. An audience of regulars might appreciate and understand where things are going in a spur of the moment post. However, in the case of "small bloggers" or new audiences, it's less likely that there will be sufficient patience to overcome the any lapses in clarity.
I cringe when I realize I've let something go too soon. I'm tempted to re-read everything and to clean it all up, but somehow I know that's not right either.
It's better to take a few minutes, read what you're about to submit aloud, and make sure you really want to say it that way.
Take the time, it'll help us all out.
Thank you for your time and attention.
--Mike--
Half-Baked Thoughts. Nobody's going to pounce on you for putting your half-baked thoughts on your blog. People may disagree, or help you see some flaws, but almost always with the understanding that they are in your house as a guest.
I respectfully disagree. An audience of regulars might appreciate and understand where things are going in a spur of the moment post. However, in the case of "small bloggers" or new audiences, it's less likely that there will be sufficient patience to overcome the any lapses in clarity.
I cringe when I realize I've let something go too soon. I'm tempted to re-read everything and to clean it all up, but somehow I know that's not right either.
It's better to take a few minutes, read what you're about to submit aloud, and make sure you really want to say it that way.
Take the time, it'll help us all out.
Thank you for your time and attention.
--Mike--
Wednesday, February 22, 2006
Virtual Machines, the future of security
The purpose of an operating system is to manage the resources of a computer. Over time, market competition has lead to the inclusion of a number of new components into standard distributions of operating systems. It is now common for such a system to include a network stack, at least one scripting language, a web browser, and email client. A server would also include services such as file sharing, authentication, web and ftp services, and more.
Windows, Mac OS, and Linux have similar security models. It's all about the user. Once the user signs in, it is assumed they should be allowed to do anything they have permission to do. The user is expected to be judicious in their choices of actions.
Unless special precautions are taken, programs run with identical permissions to the user which they are working on behalf of. This means that the user is forced to trust a program in order to use it. There is simply no other option for the average user. This need to trust code is implicit in the security model. It's so deeply embedded in our conception that it takes people by surprise when you point it out. This need to absolutely trust code is a very corrosive force, and is responsible for most of the security problems that plague PCs today.
This is how we get virii and other problems that keep cropping up, in spite of virus scanners, etc. Once lanched, a virus has essentially full run of a PC, which it can use to spread itself, or to use for its payload program.
Most efforts these days are being directed towards what I consder to be a stopgap measure. This is to try to limit the user to running only trustworthy code. The decision is made that some programmers are deemed trustworthy, and given cryptographic keys to "sign" a piece of code.
The signatures on a piece of code can thus be checked for validity before it is executed. This can help prevent tampering with the code, so it does help security, a bit.
However, this is not a long term solution, though many are otherwise convinced. The problem is that any bug, anywhere in the program can be used to attack the system. Consider that a workstation with the standard load might have a million lines of code, with perhaps 20 different services running at any give time. If any of these systems have a bug, it may be possible to exploit it, and take over the system.
--
I've been digging around the question of PC security for a while now since my Windows Apocalypse. I'm now convinced the only way out is to use a classic solution, and to head in the opposite direction.
Instead of accepting more and more code as "trusted", we need to adopt the philosophy that NOTHING should be trusted, unless absolutely necessary. Even device drivers shouldn't be trusted.
IBM engineers in the 1960s utilized the Virtual Machine concept to make scarce resources available to Operating System developers. They did this by offering what appeared to be a complete machine to each program to be run. This allowed the development of new operating systems on hardware that didn't exist yet, and eliminated the need to give each and every programmer at least one mainframe of their own.
The net result is that each and every virtual machine created is insulated from the hardware, and from every other virtual machine. It's practically impossible for a process inside a virtual machine to do any harm to the outside environment. Because of this, you don't have to trust the code you run, you can just contain it in a Virtual Machine.
The adoptation of Java, and more recently, ".net" are both steps in the right direction. They place code into a "sandbox", and limit access. However the permissions are course, and the idea of trusted code creeps in, thus limiting the effectiveness of the sandbox.
Bochs, Plex86, VMware, and "Virtual Server" are all adaptations of this strategy. They emulate a complete PC (or substantial portion thereof) to allow a complete operating system to run inside a virtual machine. This makes it possible to test out new OSs, do development, etc... much in the same way the IBM programmers back in the 1960s were allowed to do so, even though it's likely the programmers now can afford multiple computers. It's much easier to debug from an environment that doesn't have to be rebooted all the time. ;-)
The recent arrival of the "browser appliance" as a safer way to surf the web is an example of running an application insider a sandbox, albeit a very elaborate one. The speed of the virtualization on current stock hardware will be less that idea, due to some architectural limitations of the 386 heritage.
Recent announcements by both Intel and AMD of hardware support for virtualization are very encouraging. It was this type of hardware support that made the VM/370 system feasable in the 1960s. This will allow virtualization with almost no performance penalty on future machines.
The next step will be lightweight operating systems optimized to run inside virtual machines. Because the virtual machine environment provided is completely uniform, the number of drivers required to interact with it can be reduced almost to zero. As time goes on, even this overhead can be reduced by the use of run-time systems, which are tailored for specific uses.
We may start to see the distribution of applications inside of their own operating systems as a convinient means of making sure that everything necessary for the application gets included.
All of this points to a future which might make a mainframe programmer smile with the recognition that it's all happening again, but slightly differently... and they'd be right. The concept of trusted code will die, at least until the sequel. ;-)
Eventually, we'll get to the point where no application needs to be trusted. Most of the operating system itself doesn't need to be trusted, so it won't be. The long term result is to have one, and only one, piece of trusted code in the system... a microkernel virtual machine manager. It will be the only piece of code running on the bare metal. Device drivers, security algorithms, everything else will run in its own virtual environment, in complete isolation.
Only then will security be sufficiently fixed that I can relax, or so I hope.
That's my prediction, I welcome all criticism and discussion.
--Mike--
Windows, Mac OS, and Linux have similar security models. It's all about the user. Once the user signs in, it is assumed they should be allowed to do anything they have permission to do. The user is expected to be judicious in their choices of actions.
Unless special precautions are taken, programs run with identical permissions to the user which they are working on behalf of. This means that the user is forced to trust a program in order to use it. There is simply no other option for the average user. This need to trust code is implicit in the security model. It's so deeply embedded in our conception that it takes people by surprise when you point it out. This need to absolutely trust code is a very corrosive force, and is responsible for most of the security problems that plague PCs today.
This is how we get virii and other problems that keep cropping up, in spite of virus scanners, etc. Once lanched, a virus has essentially full run of a PC, which it can use to spread itself, or to use for its payload program.
Most efforts these days are being directed towards what I consder to be a stopgap measure. This is to try to limit the user to running only trustworthy code. The decision is made that some programmers are deemed trustworthy, and given cryptographic keys to "sign" a piece of code.
The signatures on a piece of code can thus be checked for validity before it is executed. This can help prevent tampering with the code, so it does help security, a bit.
However, this is not a long term solution, though many are otherwise convinced. The problem is that any bug, anywhere in the program can be used to attack the system. Consider that a workstation with the standard load might have a million lines of code, with perhaps 20 different services running at any give time. If any of these systems have a bug, it may be possible to exploit it, and take over the system.
--
I've been digging around the question of PC security for a while now since my Windows Apocalypse. I'm now convinced the only way out is to use a classic solution, and to head in the opposite direction.
Instead of accepting more and more code as "trusted", we need to adopt the philosophy that NOTHING should be trusted, unless absolutely necessary. Even device drivers shouldn't be trusted.
IBM engineers in the 1960s utilized the Virtual Machine concept to make scarce resources available to Operating System developers. They did this by offering what appeared to be a complete machine to each program to be run. This allowed the development of new operating systems on hardware that didn't exist yet, and eliminated the need to give each and every programmer at least one mainframe of their own.
The net result is that each and every virtual machine created is insulated from the hardware, and from every other virtual machine. It's practically impossible for a process inside a virtual machine to do any harm to the outside environment. Because of this, you don't have to trust the code you run, you can just contain it in a Virtual Machine.
The adoptation of Java, and more recently, ".net" are both steps in the right direction. They place code into a "sandbox", and limit access. However the permissions are course, and the idea of trusted code creeps in, thus limiting the effectiveness of the sandbox.
Bochs, Plex86, VMware, and "Virtual Server" are all adaptations of this strategy. They emulate a complete PC (or substantial portion thereof) to allow a complete operating system to run inside a virtual machine. This makes it possible to test out new OSs, do development, etc... much in the same way the IBM programmers back in the 1960s were allowed to do so, even though it's likely the programmers now can afford multiple computers. It's much easier to debug from an environment that doesn't have to be rebooted all the time. ;-)
The recent arrival of the "browser appliance" as a safer way to surf the web is an example of running an application insider a sandbox, albeit a very elaborate one. The speed of the virtualization on current stock hardware will be less that idea, due to some architectural limitations of the 386 heritage.
Recent announcements by both Intel and AMD of hardware support for virtualization are very encouraging. It was this type of hardware support that made the VM/370 system feasable in the 1960s. This will allow virtualization with almost no performance penalty on future machines.
The next step will be lightweight operating systems optimized to run inside virtual machines. Because the virtual machine environment provided is completely uniform, the number of drivers required to interact with it can be reduced almost to zero. As time goes on, even this overhead can be reduced by the use of run-time systems, which are tailored for specific uses.
We may start to see the distribution of applications inside of their own operating systems as a convinient means of making sure that everything necessary for the application gets included.
All of this points to a future which might make a mainframe programmer smile with the recognition that it's all happening again, but slightly differently... and they'd be right. The concept of trusted code will die, at least until the sequel. ;-)
Eventually, we'll get to the point where no application needs to be trusted. Most of the operating system itself doesn't need to be trusted, so it won't be. The long term result is to have one, and only one, piece of trusted code in the system... a microkernel virtual machine manager. It will be the only piece of code running on the bare metal. Device drivers, security algorithms, everything else will run in its own virtual environment, in complete isolation.
Only then will security be sufficiently fixed that I can relax, or so I hope.
That's my prediction, I welcome all criticism and discussion.
--Mike--
Subscribe to:
Posts (Atom)






