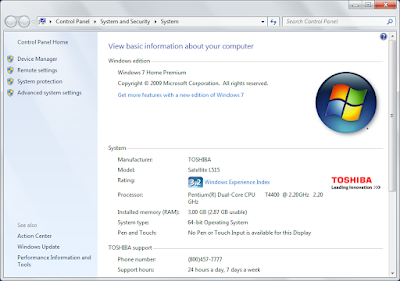
I've
declared myself to be a
super-empowered individual, on par with all of the others in that I'm going to change the world. Coming from a fat middle aged white guy, that has to be funny on a few levels. Yet I intend to change the world, in one small way, for the better.
How did I come to this absurd position? It's simple.... I got pissed off enough to change the world, and am secure enough to realize I can do it.
I'm pissed because it looks like Billions of our tax dollars are going to be sunk into "cyber security", "cyber war", etc. I'm pissed because this will be used as a justification to monitor all internet traffic, and to enable censorship.
It doesn't have to be this way. Someone has to put the brakes on, and I've decided to do it. I hope to convince you to help.
I'm going to use the tools and resources available to me, and leverage them to change the way operating systems are written. This will FIX the problem, and restore some sanity to the world of general purpose personal computing.
Computers CAN be made secure, the technology has been languishing since the 1960s, for a number of reasons. I intend to help bring it back out into general use. It is my conviction that Capability based security offers a way to make the average home computer both safe and easy to use.
The general problem with the current systems that are offered is that the user has no way to prevent a program from changing the state of his operating system. This stems from a security model that doesn't work. The user is forced to choose which programs they trust, and to only run those programs. The virus scanners, firewalls, anti-spyware, and everything else are simple aimed at helping to better chose which programs are worthy of trust.
NO program is worthy of trust. So, the systems will eventually fail. There are enough computers out there that have been compromised and turned into tools for the exploitation of the rest that any hole in the system can be leveraged and exploited by the black market.
Because no program can be trusted, you then have no choice but to "lock down" your operating system. This requires decided which features will be made available to a given program. Each program needs to have it's own set of choices, because no two programs are really going to do the same task. You have to treat each and every program as a potential trojan horse.
To make matters worse, your virus scanners and anti-spyware really can't help you, because they all rely on black lists, lists of known bad programs. This means they will always be behind in an arms race.
The current set of tools is inadequte to the task. While it's generally believed that these tools are acceptable, I believe otherwise, and I hope to prove it to you as well, so that you will help me to change the world, a bit.
Once you believe that the tools available are insufficient, the next step is to consider what the requirements are for something that would work. You need to be able to choose which resources are to be made available to a program, and how you might check post facto to make sure it did what you expect.
In the world of commerce, this is done through contract law. The court system serves to enforce contracts. It's not perfect, but it gets the job done most of the time.
Computers are much more efficient and ruthless about following rules. Any edge cases can be handled by tweaking the code, and testing it repeatedly to make sure they all work as intended. The programmer replaces the Legislative branch of government, tweaking the rules as necessary, to ensure domestic traquility.
In computing, it is the role of the operating system to enforce rules. The current system is much like the wild west, with the occaisional posse to round up malware. The rule of law is sporadically enforced.
To make things usable and transparent to the user, the rules should be as easy to build and grasp as possible. A simple list of resources to be made available to a program is sufficient. If the resource isn't on the list, the program can't have access to it. A word processor doesn't need to access much, the keyboard, mouse, screen, it's installed directory, and the file to be edited. It doesn't need access to the internet, your facebook account, tax records, etc.
This simpler model (for the end user) makes managing the resources of the computer both possible, and efficient. They can set up (or have tools to help them) defaults which make sense for everything.
Now, if you're skeptical, you might think that this really isn't different from what is offered in things like Microsoft's UAC, which crashed and burned. There are vast differences.
The UAC was security theater at its worst. It was an attempt by Microsoft to further try to blame the user, and absolve themselves of blame for our current mess by making people believe that computer security can't be solved. It made things MUCH worse than they already were, overall by destroying hope.
It's now up to us to make things right by helping to spread the word of Capability based security, and by investing some time to try it out, and to help make it work when it becomes available.
I'm just a middle aged white guy... but like everyone else, I have the resources available to change the world. A blog, friends, and time.
Thanks for your time and attention, and for your help changing the world.